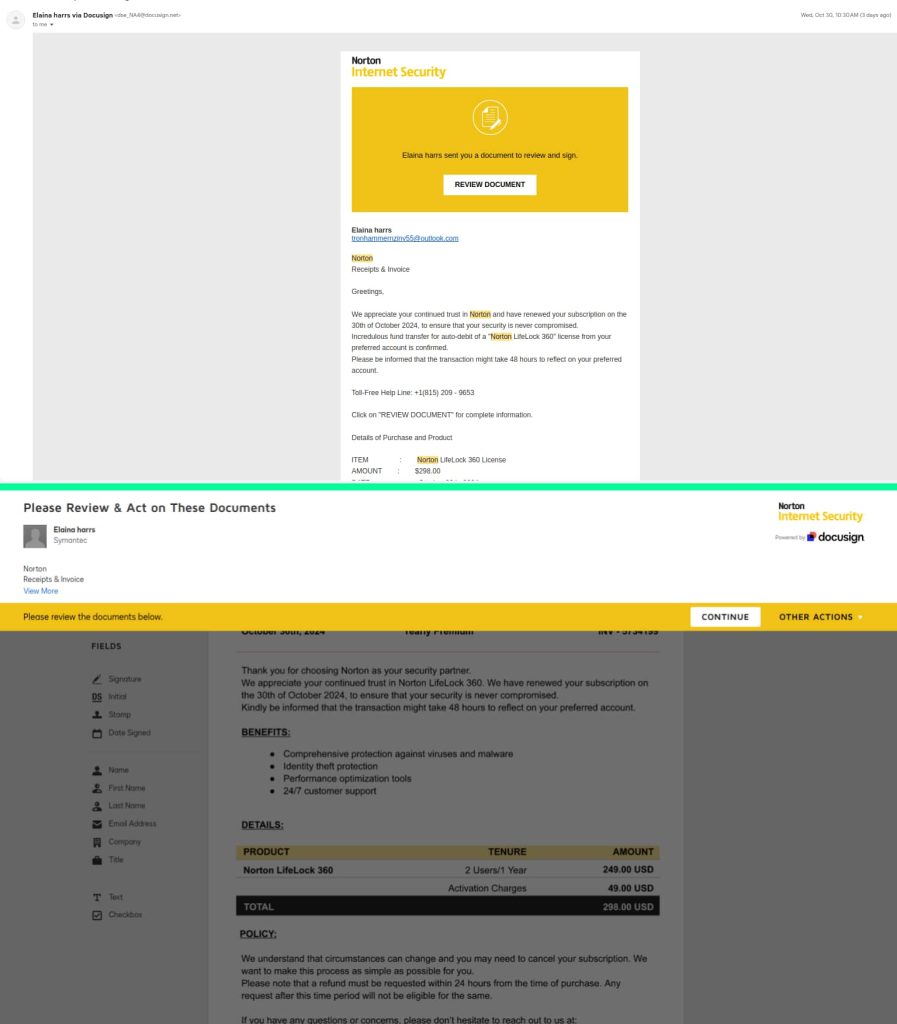
Scammers are exploiting DocuSign’s APIs to send realistic fake invoices, primarily targeting security software like Norton. This phishing technique bypasses traditional email spam filters by originating from legitimate DocuSign accounts and templates, making detection challenging.
Cybersecurity researchers at automated API security solutions provider, Wallarm, have revealed a new threat exploiting DocuSign APIs to send phishing invoices. The company reports that cybercriminals are employing a new phishing technique that leverages the legitimacy of DocuSign’s platform. By exploiting DocuSign’s APIs, attackers send highly authentic-looking fake invoices that evade traditional email filters.
This clever approach increases the risk for organizations and unsuspecting users, as it capitalizes on the trust associated with reputable platforms, making detection quite challenging.
In its latest blog post shared exclusively with Hackread.com ahead of its publishing on Monday, the modus operandi of these attacks involves the creation of paid DocuSign accounts. These accounts grant attackers the ability to modify templates and utilize APIs for automated document generation and distribution.
By customizing official DocuSign templates to mimic well-known brands, such as cybersecurity giant Norton, cybercriminals can create convincing invoices that are difficult to distinguish from legitimate communications. The automation capabilities provided by DocuSign’s APIs enable attackers to efficiently distribute these fraudulent invoices at scale, maximizing their potential impact. It happens because DocuSign’s API-friendly environment allows attackers to customize invoices to match company branding.
“These fake invoices may contain accurate pricing for the products to make them appear authentic, along with additional charges, like a $50 activation fee. Other scenarios include direct wire instructions or purchase orders,” the blog post read.
The consequences of these attacks are major. Victims may e-sign fraudulent invoices, authorizing unauthorized payments. Furthermore, the legitimacy of DocuSign’s platform allows phishing emails to bypass traditional spam filters, increasing the chance of successful delivery.
Mitigating and Protection
To mitigate the risks associated with these attacks, organizations must adopt a multi-faceted approach. Firstly, it is important to verify the authenticity of sender credentials, including email addresses and sender accounts. Implementing strict internal approval processes for financial transactions can also help prevent unauthorized payments.
Additionally, organizations should prioritize employee awareness training to educate staff about this increasing threat. By regularly monitoring for irregularities in invoices, such as unexpected charges or unusual requests, organizations can identify and respond to potential threats. Finally, following DocuSign’s anti-phishing guidelines can provide additional protection.