A new, more sophisticated variant of the FakeCall malware is targeting Android devices. Learn about the advanced features that make this malware a serious threat, including screen capturing and remote-control capabilities.
Cybersecurity researchers at Zimperium’s zLabs have identified a “Scary” new variant of the FakeCall malware. This malware tricks victims into calling fraudulent phone numbers, leading to identity theft and financial loss. FakeCall is a vishing (voice phishing) malware which, once installed, can take almost complete control of a targeted Android phone.
The latest variant exhibits several new functionalities including the ability to identify, compress, and upload image thumbnails, selectively upload specific images, remotely control the screen, simulate user actions, capture and transmit live video feeds, and remotely unlock the device. These features can capture sensitive documents or personal photos.
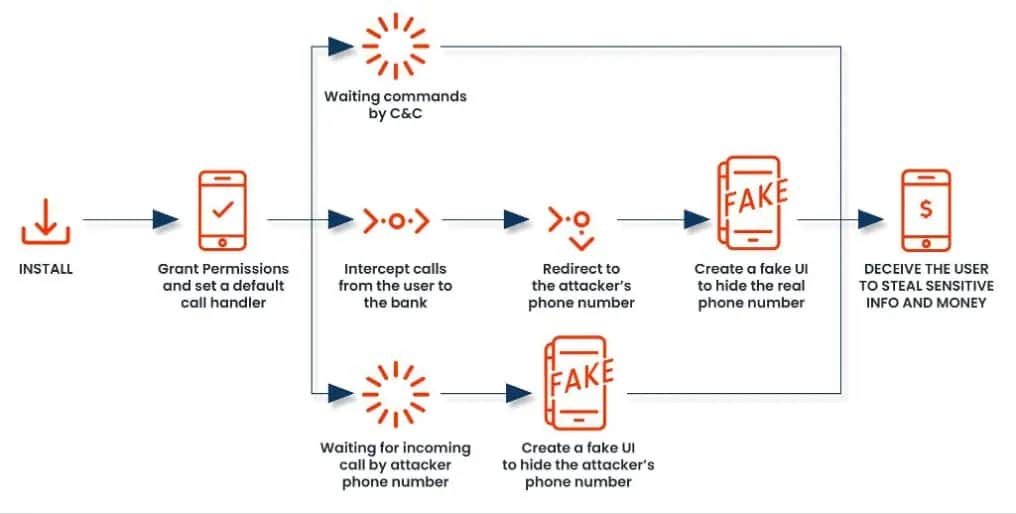
The FakeCall malware typically infiltrates a device through a malicious app downloaded from a compromised website or a phishing email. The app requests permission to become the default call handler. If granted, the malware gains extensive privileges.
According to Zimperium’s blog post shared with Hackread.com ahead of publishing on Wednesday, attackers are using a service called “The Phone Listener Service” in their attack. In fact, this service is a critical component of the malware, enabling it to manipulate the device’s calling capabilities allowing it to intercept and control all incoming and outgoing and grab sensitive information, such as one-time passwords (OTP) or account verification codes.
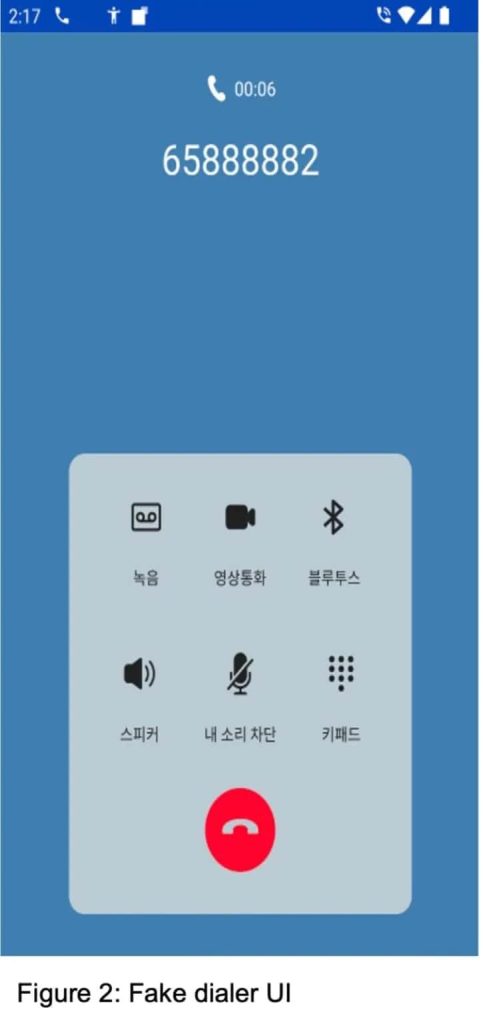
In addition, the malware can manipulate the device’s display to show fake call interfaces, tricking victims into providing sensitive information. It can also manipulate call logs to hide its malicious activity and control the duration of calls. These capabilities allow attackers to deceive victims into revealing sensitive information or transferring funds.
The malware also exploits the Android Accessibility Service to capture screen content and manipulate the device’s display to create a deceptive user interface while mimicking the legitimate phone app. This trick allows attackers to steal sensitive information, conduct surveillance, and remotely control the device.
It monitors events from the stock dialer app and detects permission prompts from the system permission manager and system UI. Upon detecting specific events, it can grant permissions for the malware, bypassing user consent. The malware allows remote attackers to control the victim’s device UI, allowing them to simulate user interactions and precisely manipulate the device.
On the other hand, the good news is that Google has already investigated the apps affected by the Scary malware imitation. Google informed Hackread.com that all apps on Google Play are protected from the new variant.
“Based on our current detection, no apps containing this malware are found on Google Play. Android users are automatically protected against known versions of this malware by Google Play Protect, which is on by default on Android devices with Google Play Services. Google Play Protect can warn users or block apps known to exhibit malicious behaviour, even when those apps come from sources outside of Play.”
A Google spokesperson
To protect against such malware, always download apps from trusted sources like Google Play Store, be cautious about permission requests, and use mobile security software with on-device detection capabilities.
RELATED TOPICS
- Unicode QR Code Phishing Scam Bypasses Traditional Security
- Malware Attack Imitates VPN, Security Apps on Android Phones
- Antidot Android Malware Poses as Google Update to Steal Funds
- QR Code Scam: Fake Voicemails Hits Users, 1000 Attacks in 14 Days
- Advanced Vishing Attack Campaign “LetsCall” Targets Android Users