They call it Shellshock bug, they say it is way more dangerous than the previous Heartbleed bug which left all the secure SSL system vulnerable, but this bug has power to compromise any system and run commands to install malicious softwares on your device or computer.
Hackers may already be accessing people’s personal data by exploiting a massive security flaw affecting hundreds of millions of computers and other devices across the world.
We are going to discuss what this Shellshock bug can do and which systems (OS) are under attack.
1. The Shellshock is a Bash bug able to find a way to exploit any operating system, doesn’t matter if it’s Apple Mac OS X or Linux operating systems.
2. It sends and executes command to the infected system through a malicious code.
3. The terminal area which infects the system is usually blocked for access, but Shellshock Bash bug can open all the terminals of a system.
RELATED STORY: Your email Password, Credit Card at Risk Web Encryption Compromised by Heart Bleed Bug
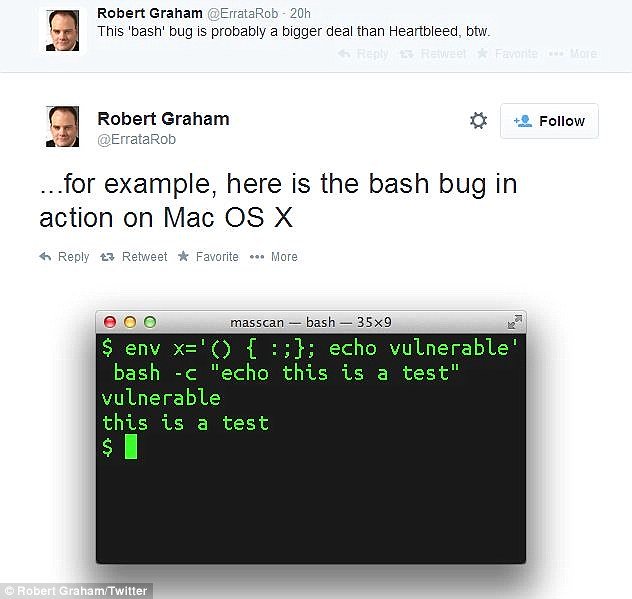
A security researcher on Twitter going with the handle of @ErrataRob shows how this bug runs on Mac OS X.
Here is a shocker for you: This bug doesn’t affect Windows operating system. Yes! It doesn’t but if an attacker is able to run the malicious code, it can get the access of computer devices. A working working example is when an Apache Web Sever runs bash command to process task along with the data entered in the online forms.
RELATED STORY: KALI Linux Website Hacked Using Heartbleed Bug
At the moment there is no update from the companies owning the above discussed OS. However, government of US and the UK has issued national alerts in response to the bug, warning that it may compromise organisations responsible for critical national infrastructure such as power stations if it is not rapidly dealt with.
A good explanation about this bug has been given in the video below:
In a statement issued today the ICO said:
The Shellshock flaw could be allowing criminals to access personal data held on computers or other devices, which should be ringing real alarm bells. The worst thing would be to think this issue sounds too complicated businesses need to be aware of this flaw and need to be monitoring what they can do to address it. Ignoring the problem could leave them open to a serious data breach and ultimately, enforcement action.
Who found this bug?
This bug was originally discovered by a 38-year-old French software developer Stephane Chazelas, living in Edinburgh. This Flaw uncovered by chance, he said to The Independent Today.
A report suggests that this bug was in the market for last 25 years and chances are that hackers have been using it to infect million of users online. Another report reveals that Apple had already fixed this bug but never revealed that its OS was vulnerable to this bug.
RELATED STORY:Heartbleed now reforms into Cupid attack targeting Wi-Fi networks and Android
Stay with us, we will update the article with new information on the Shellshock Bash bug soon.
The difference between the previous Heartbleed attack and in this type of attack is that the TLS connection runs on EAP, which is an authentication framework used in Wi-Fi networks. EAP also used in wired networks and Peer to Peer connection.
In this attack, the types of EAP used are EAP-PEAP, EAP-TLS, and EAP-TTLS. All these EAP use TLS connection.
For a successful attack on vulnerable clients, attackers use hostapd (with the cupid patch) to set a malicious network. When the vulnerable client attempts to connect via sending request to TLS connection, the hostapd will in reply send malicious heartbeat request with vulnerability.
Author Bio:
Jason Parms is working as an Internet Marketing Manager at SSL2BUY Inc. He is specialized in implementing and creating online marketing strategies and spread the brand awareness over the web. Apart from the core profession, he also takes interest in subjects of cyber security, web security development, cyber crime, and hacking.