Editor’s Note (Updated): This article has been edited to reflect clarifications provided by Resecurity, including the company’s December 24 statement from last year, that the accessed environment was part of a honeypot containing only synthetic and inactionable data. A separate, updated article covering the incident has also been published, titled: Resecurity Says ShinyHunters Fell for Honeypot After Breach Claim.
The hacking group ShinyHunters has claimed responsibility for breaching Resecurity, a US-based cybersecurity company headquartered in Los Angeles. In a public Telegram post shared earlier today, the group announced it had gained full access to internal systems and released a set of screenshots to support its claim.
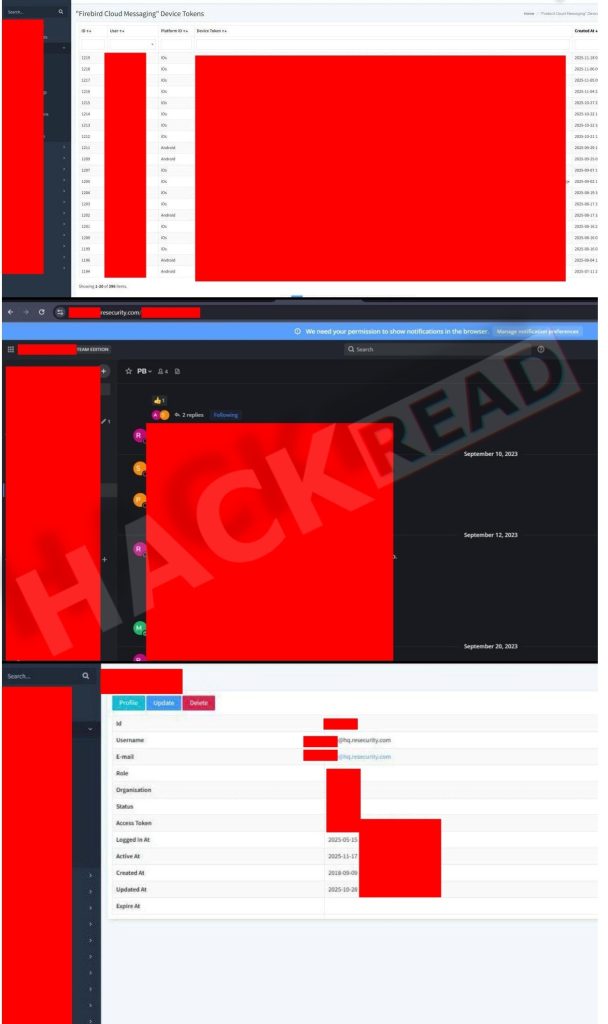
The images depict several internal Resecurity dashboards, user management panels, token databases, and employee communication channels. The interfaces shown include sensitive user data, API keys, access tokens, and internal Mattermost chat conversations.
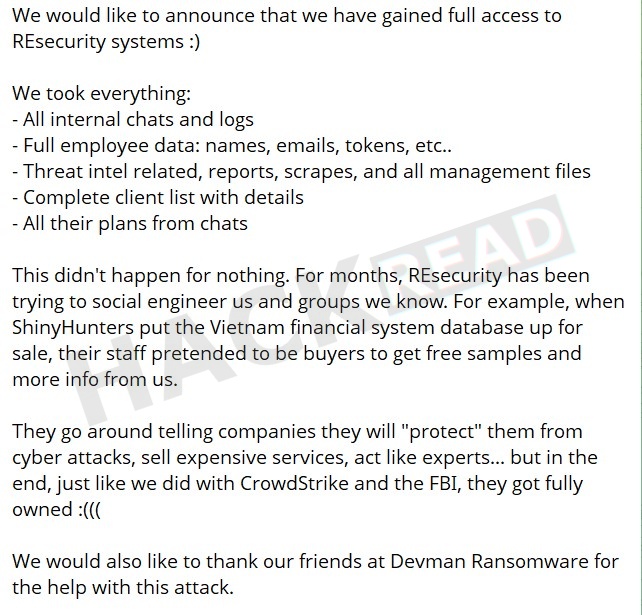
In their post, ShinyHunters claimed they exfiltrated:
- Full internal chats and logs
- Internal plans discussed in chat logs
- A complete client list with related details
- Threat intelligence data, reports, and management documents
- Employee information, including names, email addresses, and authentication tokens.
The screenshots shared by the hackers were analysed by Hackread.com, showing content which, according to Resecurity, originated from a honeypot environment containing only synthetic and inactionable data.
They also mentioned collaboration with the Devman ransomware group in executing the attack. The post references prior claims involving other high-profile breaches, such as CrowdStrike, framing this incident as part of a continued effort targeting firms they label as hypocritical or deceptive.
Resecurity is successfully collaborating and continues to collaborate with both government and private sector entities in cybercrime investigation, threat attribution, and digital forensics. More information is expected as the situation develops.
Update:
Following the publication, Resecurity responded and clarified that the environment accessed by the threat actor was part of a controlled honeypot operation. According to the company, synthetic data and decoy applications were deployed intentionally to monitor malicious activity, with no link to real customer systems or internal operations.
Resecurity stated there was no data loss, no exposure of actual passwords, and no impact on clients. They also published a detailed log of the attacker’s activity, including a screenshot showing multiple entries tied to the fake honeypot email address [email protected], along with IP addresses and endpoint requests. The screenshot further supports their claim that the actor was interacting with a decoy system rather than any production environment.
More on this is available here.