Domain Hijacking Alert! Hackers easily redirect you to fake websites using the newly discovered Sitting Ducks attack. Protect yourself from phishing & data breaches. Learn how to stay safe online!
Cybersecurity researchers at Infoblox and Eclypsium have collaborated and discovered a sophisticated attack vector in the Domain Name System (DNS), dubbed the Sitting Ducks attack. The attack was disclosed while studying the infrastructure used for the 404TDS, a Russian-hosted traffic distribution system, indicating the involvement of Russian-nexus cybercriminals.
Sitting Ducks is a DNS-related issue first detected in August 2016 by Matt Bryant. Reportedly, a new exploitation threat has been targeting users worldwide since June 2024.
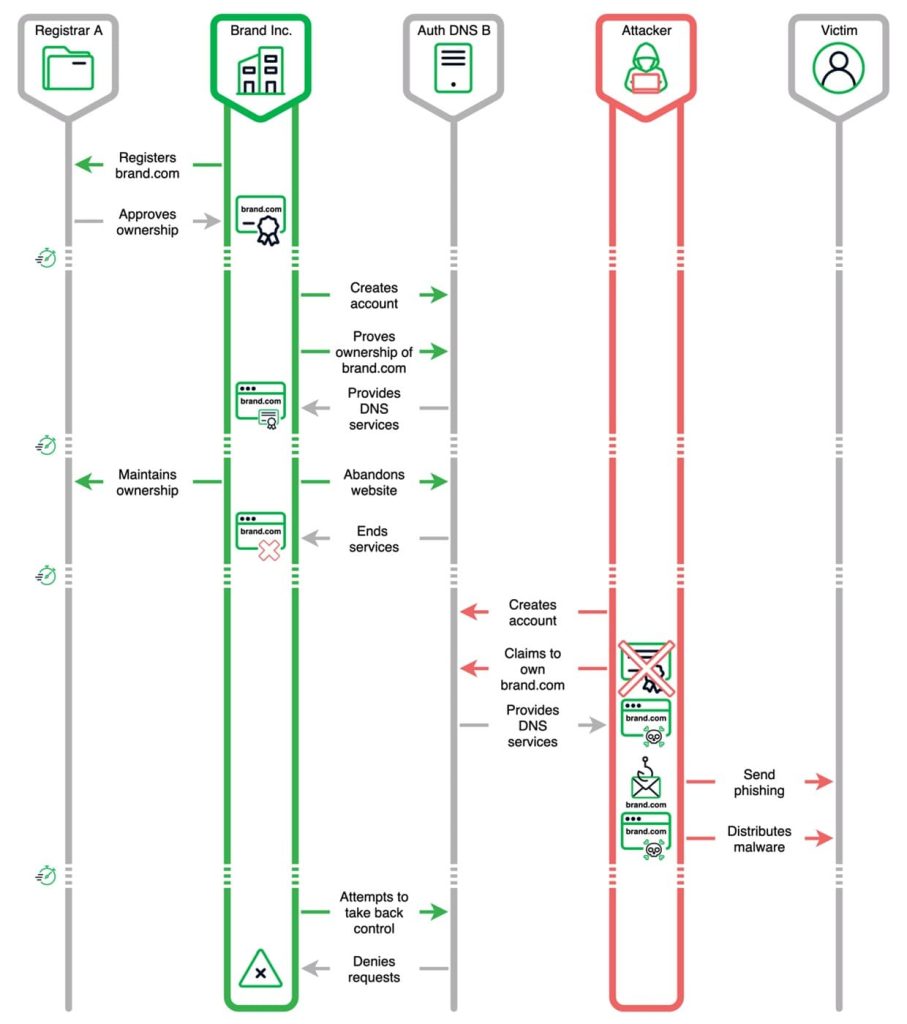
The attack is different from other domain control techniques as registrar access is not required and all the attackers need is lame delegation. Delegation occurs when a registered domain or subdomain delegates authoritative DNS services to a different provider than the domain registrar, and it becomes lame when the authoritative name server(s) lack domain information and cannot resolve queries. A lame delegation attack occurs when a malicious actor registers the assigned domain, gaining access to all domains pointing to that domain.
Additionally, attackers exploit DNS provider vulnerabilities by scanning the internet for domains with lame delegations, claiming ownership without proper authorization. They create a malicious record for the hijacked domain, redirecting traffic to a malicious server, and redirecting users to the attacker’s site.
According to Eclypsium’s blog post, Sitting Ducks have several variations. It can exploit typos in the domain owner’s name server information, enabling active attacks to register partially lame domains. Dangling DNS records, containing invalid information due to forgotten configuration, can be generalized to other DNS record types. Dangling CNAME attacks redirect DNS responses to lapsed domain names, allowing malicious actors to register lapsed domains and gain pedigree.
A large-scale analysis of domain delegations and evaluation of about a dozen DNS providers revealed multiple actors, most prominently Russian cybercriminals, are using this attack, and hundreds of domains are hijacked daily, often registered with brand protection registrars or lookalike domains.
“Our research revealed that the Sitting Ducks vector has been used to hijack over 35k domains since 2018, although the true number is likely much higher,” Infoblox’s report read.
The consequences of this attack can be severe. Attackers can perform malicious activities under the guise of the legitimate owner, including malware delivery, phishing campaigns, brand impersonation, and data exfiltration. With over 1 million exploitable target domains and multiple methods available to detect such domains, the attack is easy to perform, almost unrecognizable, and entirely preventable, researchers noted.
These are preventable because the attack is possible due to gaps in domain name and DNS records management, considering that DNS misconfigurations are often overlooked as a strategic attack surface and published attack vectors against DNS are dismissed as inevitable.
To prevent Sitting ducks, domain owners should use an authoritative DNS provider independent of their domain registrar to avoid Sitting Ducks attacks. Ensure domains and subdomains have name server delegation to invalid service providers, and inquire about DNS provider mitigations to reduce risk.
RELATED TOPICS
- New Soap2day Domains Emerge Despite Legal Challenges
- DNS Tunneling Used for Stealthy Scans and Email Tracking
- “Revolver Rabbit” Uses RDGA to Register 500,000 Domains
- Breach Forums Admin ShinyHunters Reclaims Domain from the FBI
- DeFi Hack Alert: Squarespace Domains Vulnerable to DNS Hijacking
- Over 800 Phony “Temu” Domains Lure Shoppers into Credential Theft