Security breaches are not only technical problems but also personal, financial, and reputational crises. In software development, particularly in backend systems and infrastructure, it’s clear that old threats often resurface with new and evolving consequences.
One of the most persistent? SQL injection.
It may sound like a relic of the early 2000s, but in 2025, it’s still wreaking havoc. According to IBM’s Cost of a Data Breach Report, injection attacks ranked among the top five most exploited vectors, contributing to over 23% of breaches analyzed.
This isn’t a failure of tooling, but it’s a failure of attention. The threat persists not because we lack the means to stop it, but because we too often assume we’ve already won.
What Makes SQL Injection So Dangerous?
Simply put, SQL injection is deceptively simple. It involves inserting malicious content into user inputs that interact with backend databases.
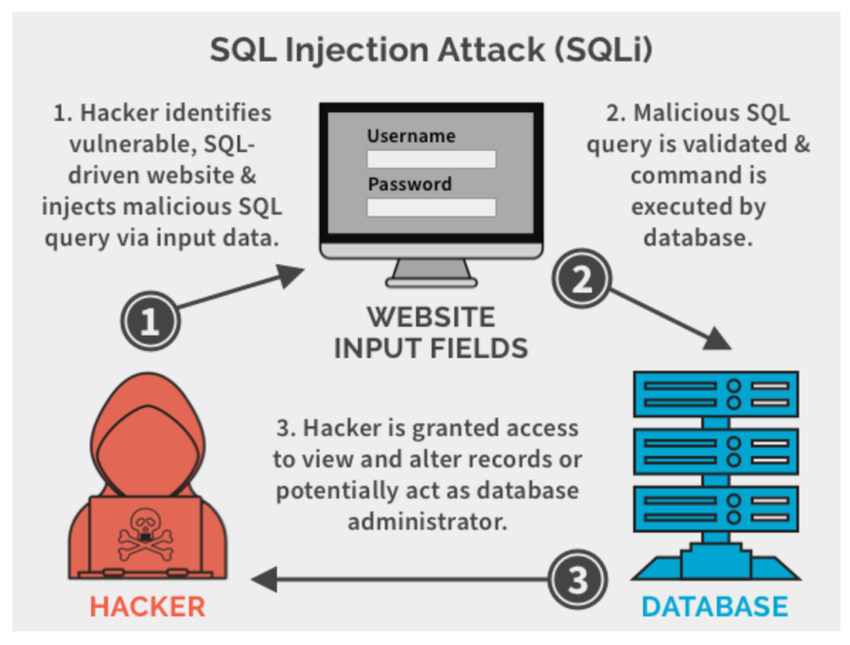
When input fields aren’t properly validated or sanitized, attackers can manipulate database queries to access, alter, or delete sensitive information, or even gain administrative control. What makes SQL injection especially dangerous is how much damage can stem from something as simple as an unsecured form field.
Small oversights in input handling can compromise entire systems. In large-scale commercial environments, complex workflows such as customer registration and order tracking are often simplified while ensuring the underlying security is rigorously enforced. Every field is reviewed, tested, and monitored with care because the stakes are far too high to get it wrong.
The Real-World Impact of Breaches
SQL injection isn’t just a technical flaw; it’s a direct risk to people’s data and trust. One of the most damaging early examples came in 2007 when a 7‑Eleven Hack From Russia led to ATM Looting in New York. The attackers captured magnetic stripe data and PIN codes from customers’ debit cards, which were then used to create counterfeit cards. Over just three days, criminals withdrew approximately $180,000 from ATMs in New York, part of a broader operation that affected multiple U.S. companies and compromised millions of cards.
Breaches like this don’t just break systems, they break confidence. Once trust is lost, it’s nearly impossible to win back. That’s why secure code isn’t a feature; it’s a responsibility.
Why SQL Injection Is Still Prevalent in 2025
There’s a common misconception that SQL injection is a thing of the past. Today’s frameworks and best practices warn against unsafe query handling, yet the pace of digital transformation often outpaces secure implementation. Whether in high-frequency trading platforms or scalable cloud-native applications, one truth remains: security can never be assumed.
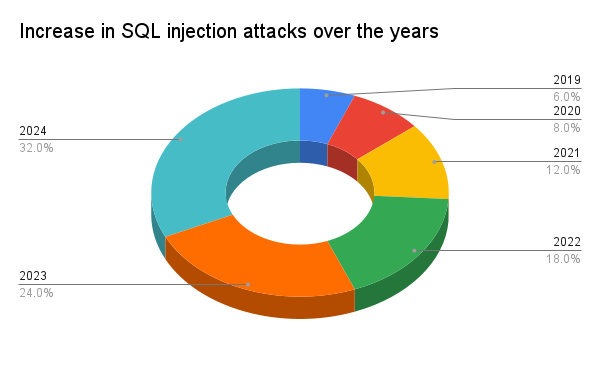
As the chart shows, SQL injection attacks have risen steadily over the past five years, from just 6% in 2019 to 32% in 2024. This isn’t just an outlier; it’s a trend. And it signals a future where, unless security is prioritized at every stage of development, the problem will only worsen.
SQL injection remains relevant because:
- Many legacy systems still rely on outdated practices or hardcoded SQL statements.
- Developers working under tight deadlines sometimes bypass security checks.
- Small businesses and startups often lack dedicated security resources.
- Open-source libraries, if not regularly audited, can introduce hidden vulnerabilities.
Even large organizations aren’t immune. Something as small as an unvalidated input field in a backend system can become an entry point for SQL injection.
Best Practices to Reduce SQL Injection Risk
Across roles in domains ranging from fintech systems to high-scale e-commerce, one lesson remains consistent: preventing SQL injection starts with disciplined, consistent practices. Below are some of the most effective security measures used and recommended in production environments:
- Input Validation & Sanitization: Ensures only clean, expected data enters your system.
- Principle of Least Privilege: Limits access to only what each system or user needs.
- Input Whitelisting: Defines which data formats are allowed, rather than just blocking bad input.
- Error Message Suppression: Prevents internal system details from being exposed to attackers.
- Anomaly Monitoring & Logging: Detects suspicious activity before it becomes a full-blown breach.
- Regular Security Audits & Training: Keeps teams aligned on secure development practices.
These measures are not just theoretical. Each has been implemented in real production environments. The goal in every case is simple: reduce the attack surface, catch vulnerabilities early, and build resilient systems from the ground up.
Smart Security: Why AI Alone Isn’t Enough in the Cloud
The rise of artificial intelligence and machine learning has transformed how we detect and respond to security threats like SQL injection. These technologies are now embedded into modern security workflows, analyzing data access patterns and flagging anomalies before they escalate into breaches. The same algorithmic principles that drive fault tolerance and resilience are now enabling systems to self-heal and adapt in real-time to evolving threats.
But while AI helps us detect attacks faster, it’s not a silver bullet, especially in the cloud. Many companies still assume that moving to cloud infrastructure reduces their security responsibilities. In reality, it only shifts them.
Cloud-native platforms, such as Lambda, Step Functions, and DynamoDB, offer flexibility and scalability, but only when paired with rigorous security practices. That means continuously auditing configurations, enforcing least privilege, and integrating intelligent monitoring tools that flag risky behaviour in real-time.
AI may enhance our security, but it’s disciplined cloud architecture and vigilant oversight that truly keep systems secure.
Final Thoughts: Empathy Is at the Heart of Secure Engineering
Security isn’t just a checklist; it’s a mindset. It’s about caring deeply for the people who trust us with their data. Whether building systems for millions of customers or participating in research on secure ledgers, the goal remains the same: to build systems that are robust, ethical, and resilient.
SQL injection may be one of the oldest tricks in the book, but it’s also one of the most dangerous. It thrives on complacency and thrives where speed is valued over security.
Disclaimer: All thoughts and opinions expressed are solely my own and do not represent the views of any company, employer, or affiliated entity. But one thing remains clear: if we, as engineers and decision-makers, prioritize empathy, diligence, and continuous learning, we can prevent the next big breach and protect the data that defines modern life.
References
Amazon Web Services (n.d.). Amazon DynamoDB. https://aws.amazon.com/dynamodb/
Amazon Web Services (n.d.). AWS Lambda: What is AWS Lambda? https://docs.aws.amazon.com/lambda/latest/dg/welcome.html
Amazon Web Services (n.d.). AWS Step Functions: What is Step Functions? https://docs.aws.amazon.com/step-functions/latest/dg/welcome.html
Cyserch (2025). SQL Injection in 2025: How One Vulnerability Can Expose Your Business Data. https://www.cyserch.com/blog/SQL-Injection-in-2024:-How-One-Vulnerability-Can-Expose-Your-Business-Data
IBM (2024). Cost of a Data Breach Report 2024. https://www.ibm.com/reports/data-breach
Imperva (n.d.). SQL (Structured Query Language) Injection: What is SQL injection? https://www.imperva.com/learn/application-security/sql-injection-sqli/
Research Gate (2023). Big Data and Cognitive Computing (BDCC). A New Approach to Data Analysis Using Machine Learning for Cybersecurity. https://www.researchgate.net/publication/375811584_A_New_Approach_to_Data_Analysis_Using_Machine_Learning_for_Cybersecurity
Wired (2009). Security: 7-Eleven Hack From Russia Led to ATM Looting in New York. https://www.wired.com/2009/12/seven-eleven/