EvilVideo exploit in Telegram for Android lets attackers send malware disguised as videos. ESET discovered this zero-day vulnerability, prompting Telegram to release a security patch in version 10.14.5. Update now!
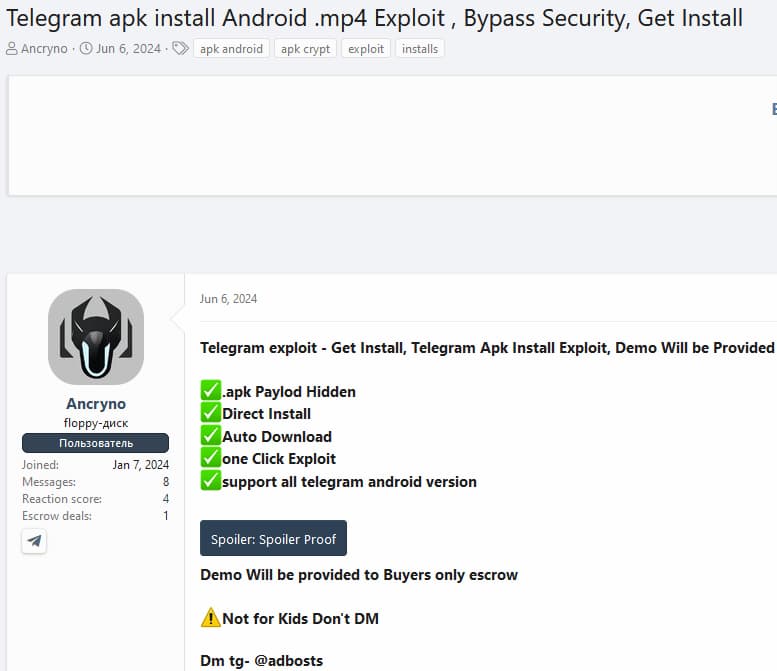
ESET cybersecurity researchers have identified a zero-day exploit targeting Telegram for Android, dubbed “EvilVideo,” which was found for sale on the Russian underground forum XSS.IS on June 6, 2024. This exploit allows attackers to distribute malicious Android payloads disguised as video files via Telegram channels, groups, and chats.
The discovery of this exploit led to a thorough analysis by ESET, resulting in a detailed report to Telegram on June 26, 2024. However, details of the vulnerability were only published today, July 22, 2024.
According to the report, Telegram responded promptly to ESET’s disclosure and released an update on July 11, 2024, that patched the vulnerability in versions 10.14.5 and above.
ESET discovered the EvilVideo exploit being advertised on an underground forum, where the seller provided screenshots and a video demonstrating the exploit in a public Telegram channel. This information allowed ESET to track down the channel and obtain the payload for further testing.
The analysis revealed that the exploit affects Telegram versions 10.14.4 and older. The payload, likely crafted using the Telegram API, masquerades as a multimedia file. When shared in a chat, the malicious payload appears as a 30-second video. By default, Telegram automatically downloads media files, meaning that users with this setting enabled would automatically download the malicious payload upon opening the conversation.
If a user attempts to play the “video,” Telegram displays an error message suggesting the use of an external player. Tapping the Open button in this message prompts the installation of a malicious app disguised as an external player. Telegram will then request the user to enable the installation of unknown apps, which leads to the installation of the malicious app.
Testing on Other Platforms
ESET tested the exploit on other Telegram clients, including Telegram Web and Telegram Desktop for Windows, and found that the exploit did not work on these platforms. Both clients displayed error messages and treated the payload as a multimedia file, preventing the exploit from executing.
The threat actor behind EvilVideo also offers an Android cryptor-as-a-service, claiming it is fully undetectable (FUD). This service has been advertised on the same underground forum since January 11, 2024.
Disclosure and Patch
ESET reported the EvilVideo vulnerability to Telegram on June 26, 2024, and again on July 4, 2024, after receiving no initial response. Telegram confirmed they were investigating the issue and released a patch on July 11, 2024, with version 10.14.5. The patch ensures that shared files are correctly identified as applications rather than videos.
ESET’s discovery of the EvilVideo exploit shows that complete security is impossible, and even popular messaging platforms are vulnerable to zero-day exploits. However, due to ESET’s timely intervention and Telegram’s quick response, the vulnerability has been patched. Telegram users on Android should update their app to the latest version to protect against EvilVideo and similar threats.
RELATED TOPICS
- Triada Malware Infects Android Devices via Fake Telegram App
- Telekopye Toolkit Used as Telegram Bot to Scam Marketplace Users
- Chinese APT Slid Fake Signal, Telegram Apps onto Official App Stores
- Legion: Credential Harvesting, SMS Hijacking Malware Sold on Telegram
- Fake Telegram and WhatsApp clones aim at crypto on Android, Windows