Meet TgRat Trojan: Once known for targeting Windows devices, the new version targets Linux and runs its command and control center through the popular messaging app Telegram.
Cybersecurity experts at Dr. Web have found a sophisticated Linux-based Remote Access Trojan (RAT) called TgRat, which uses a clever disguise: it’s controlled through a private Telegram chat.
This malware, which allows cybercriminals to remotely control infected machines, exfiltrate data, and execute commands, was initially discovered in a Windows version two years ago but has now been adapted to target Linux environments.
The TgRat trojan operates by connecting to a Telegram bot, a method that takes advantage of the popular messaging platform’s widespread use in corporate settings. This unique control mechanism enables attackers to issue commands to the infected system secretly, making it difficult for victims to detect the infection.
Upon infection, TgRat checks to confirm it is running on a targeted machine by comparing the computer’s name hash against an embedded string. If the values do not align, the malware self-terminates, avoiding detection. If it does match, the trojan connects to the Telegram bot and awaits further instructions from its operators.
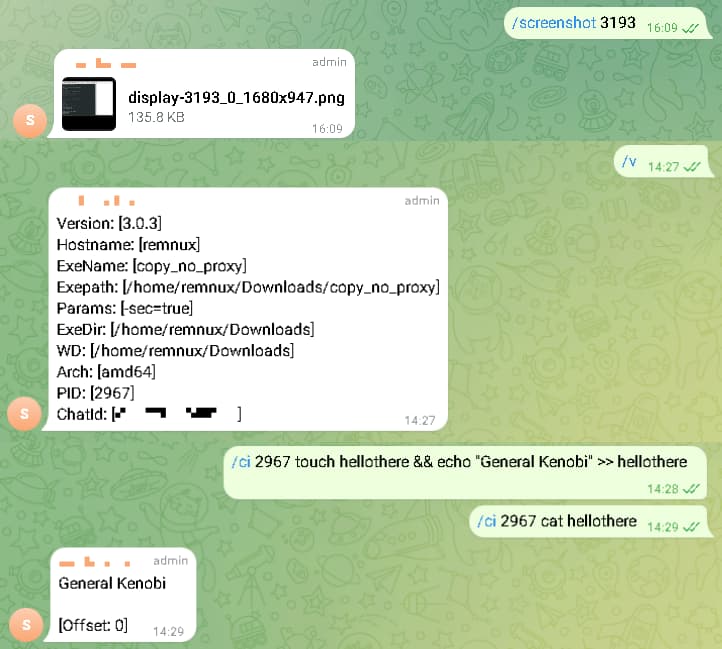
Once established, TgRat can execute various malicious activities, including downloading files, taking screenshots, and running commands remotely. Its design allows for the execution of entire scripts through a single message, enhancing its effectiveness and stealth.
According to Dr. Web’s blog post, the discovery came after a hosting provider reported suspicious activity, prompting Doctor Web’s virus lab to investigate. They found a trojan dropper that installed the TgRat malware on the server, leading to further analysis of its capabilities.
Experts warn that the use of Telegram for command and control makes this trojan particularly stealthy. The regular traffic to Telegram’s servers can easily disguise malicious communications, complicating detection efforts for network security teams.
While the TgRat trojan is a sophisticated threat, cybersecurity professionals can identify its activity by monitoring network traffic. Unusual exchanges with Telegram servers from local network devices can signal a potential compromise, allowing for timely intervention.
RELATED TOPICS
- Phishers Now Actively Automating Scams with Telegram
- Telegram Android Flaw “EvilVideo” Sends Malware as Videos
- Triada Malware Infects Android Devices via Fake Telegram App
- Telekopye Toolkit Used as Telegram Bot to Scam Marketplace Users
- Chinese APT Slid Fake Signal, Telegram Apps onto Official App Stores









