Sneaky 2FA: New Phishing-as-a-Service targets Microsoft 365, leveraging sophisticated evasion techniques and a Telegram-based platform to steal credentials.
In December 2024, during routine threat hunting activities, Sekoia.io uncovered a new Adversary-in-the-Middle (AiTM) phishing kit specifically targeting Microsoft 365 accounts. This phishing kit, dubbed Sneaky 2FA, has been circulating since at least October 2024, with potential compromises identified through Sekoia.io telemetry.
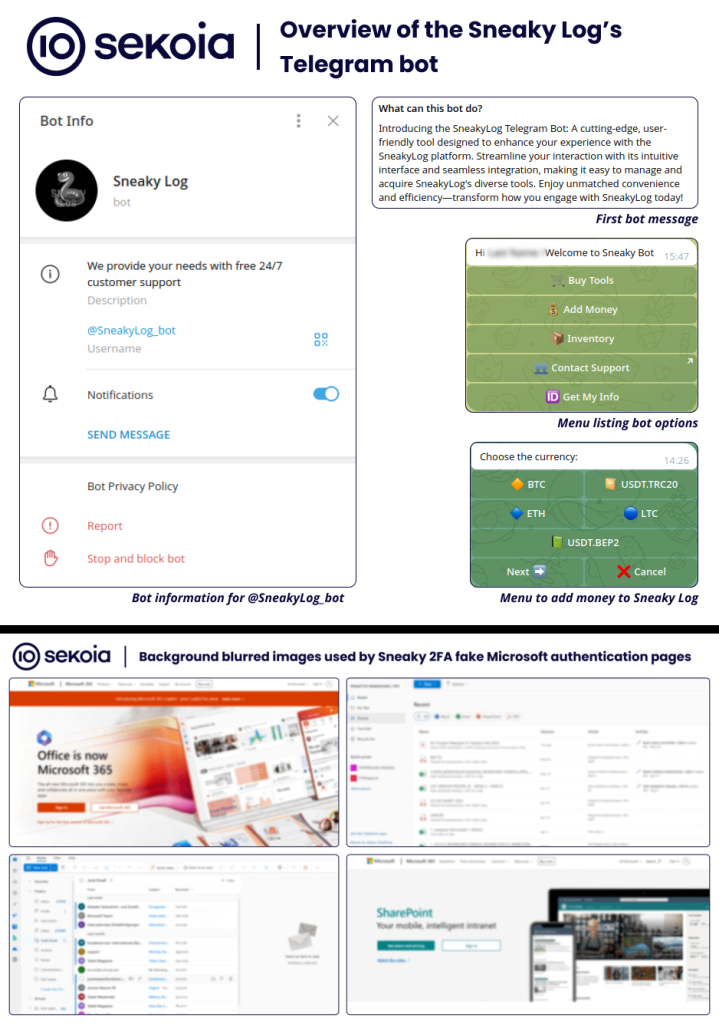
Further probing revealed that Sneaky 2FA is being offered as a Phishing-as-a-Service (PhaaS) by the cybercrime service “Sneaky Log,” which operates through a fully-featured bot on Telegram.
The modus operandi of the entire campaign includes customers receiving access to a licensed and obfuscated source code version, allowing them to independently deploy phishing pages, typically hosted on compromised infrastructure, frequently involving WordPress websites and other domains controlled by the attackers.
In addition, the Sneaky 2FA phishing kit incorporates elements from the W3LL Panel OV6, another AiTM phishing kit previously reported by Group-IB. This connection suggests a possible lineage and development within the cybercriminal infrastructure.
Characteristics of Sneaky 2FA
According to Sekoia’s report, the Sneaky 2FA phishing kit employs several techniques to evade detection and enhance its success. It utilizes URL patterns, such as “mysilverfox.commy/00/#victimexamplecom,” to automatically prefill the phishing page with the victim’s email address.
These phishing URLs are generated using 150 alphanumeric characters, followed by the path /index, /verify, and /validate. This pattern offers opportunities for tracking. Most customers deploy the server in a dedicated repository, named /auth/ by default.
To further enhance its stealth, Sneaky 2FA integrates anti-bot and anti-analysis features. Cloudflare Turnstile pages are employed to differentiate human users from bots. These pages often present seemingly benign content before loading the actual challenge. Additionally, the phishing kit incorporates anti-debugging techniques to hinder analysis using web browser developer tools.
The phishing pages themselves utilize a variety of obfuscation methods, including HTML and JavaScript code obfuscation, the embedding of text as images, and the inclusion of junk data within the HTML code. These techniques aim to make phishing pages more difficult to detect by security tools.
Sneaky Log’s Operations
The Sneaky Log service operates through a sophisticated Telegram bot that allows customers to purchase the phishing kit, manage subscriptions, and receive support. The bot offers a user-friendly interface and supports multiple cryptocurrency payment options, including Bitcoin, Ethereum, and Tether.
Analysis of cryptocurrency transactions revealed potential money laundering activities, with users instructed to pay a 10% premium and subsequent transfers occurring between various addresses.
Detection and Tracking Opportunities
Detecting Sneaky 2FA attacks can be achieved by analysing authentication logs for anomalies. The phishing kit utilizes inconsistent User-Agent strings for different stages of the authentication process, which can be identified as “impossible device shifts” and flagged as suspicious activity. Furthermore, the analysis of phishing page URLs, including patterns and domain registrations, can help track and identify campaigns associated with Sneaky 2FA.
Sneaky 2FA is a growing threat in Microsoft 365 phishing attacks, offering sophisticated features and a user-friendly PhaaS platform. To mitigate risks, organizations must continuously monitor and share threat intelligence apart from improving cybersecurity measures.
Stephen Kowski, Field CTO at Pleasanton, Calif.-based SlashNext Email Security+ commented on this urging Microsoft 365 to remain alert. “This kit’s ‘sneaky’ aspects include its sophisticated ability to populate victim email addresses automatically, its evasion of detection through Cloudflare Turnstile challenges, and its clever redirection of security tools to Wikipedia pages.“
“The kit is a full-featured PhaaS platform with real-time credential and session cookie theft capabilities, making it particularly dangerous for Microsoft 365 environments,“ Stephen warned. “Protection requires phishing-resistant authentication methods like FIDO2/WebAuthn, real-time URL scanning at the time of click that completely bypasses Cloudflare Turnstile protection and proactive detection of newly registered phishing domains before they become active threats.“
RELATED TOPICS
- Malware Bypasses MS Defender, 2FA to Steal $24K in Crypto
- Rockstar 2FA Phishing-as-a-Service Kit Hits MS 365 Accounts
- Dark Web Anti-Bot Services Let Phishers Bypass Google’s Red Page
- New Telekopye Scam Toolkit Targeting Booking.com and Airbnb Users
- Malware Exploits Avast Anti-Rootkit Driver to Disable Security Software