Urgent alert for PHP users: Update your server immediately to protect against the newly exploited CVE-2024-4577 by TellYouThePass ransomware.
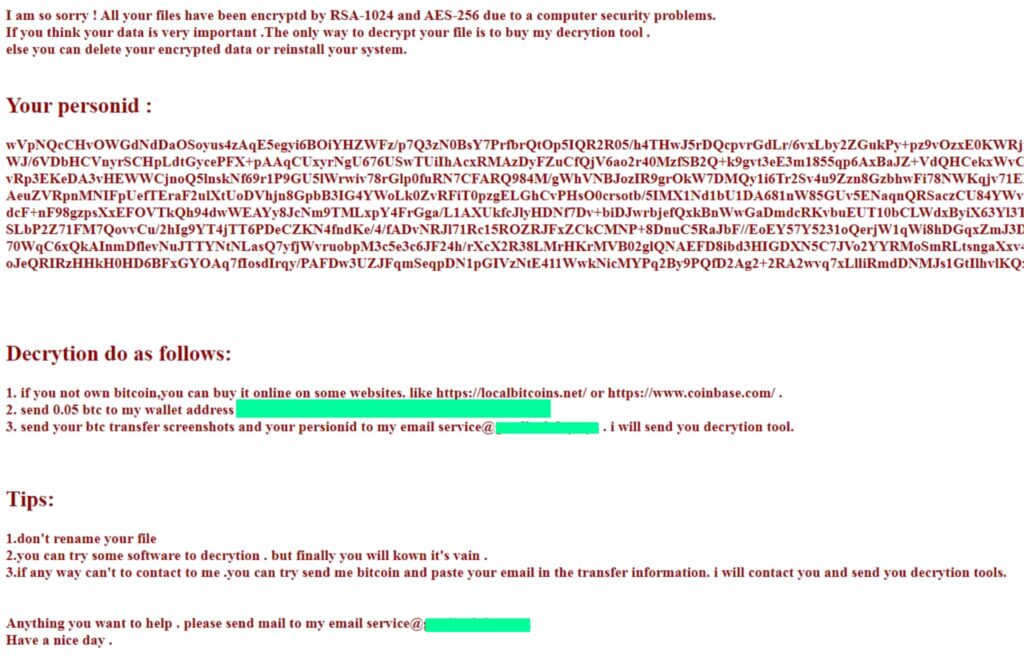
According to recent research from Imperva, the notorious TellYouThePass ransomware gang is exploiting a high-severity flaw in PHP. This vulnerability, identified as CVE-2024-4577, allows unauthenticated attackers to execute arbitrary code on vulnerable PHP installations, posing a major threat to organizations that have not yet patched their systems.
TellYouThePass is a ransomware active since 2019, targeting both businesses and individuals on Windows and Linux systems. It often exploits the Apache Log4j vulnerability (CVE-2021-44228) and has also been observed using CVE-2023-46604, among other vulnerabilities.
The TellYouThePass ransomware operators wasted no time in capitalizing on this vulnerability. Imperva researchers discovered that the gang began exploiting this PHP bug mere hours after a proof-of-concept (PoC) exploit was made public on June 10, 2024. The threat actors target exposed PHP servers to gain initial access, then move laterally through victims’ networks before encrypting files and demanding ransom payments.
In response to this threat, PHP developers have released security updates addressing the RCE vulnerability in versions 8.2.7, 8.1.19, and 7.4.33. System administrators are strongly advised to upgrade their PHP installations to these latest patched releases to protect against potential attacks.
Commenting on the issue, Agnidipta Sarkar, Vice President of CISO Advisory at ColorTokens, highlighted the urgency of the situation. “The TellYouThePass ransomware campaign, which has added this CVE to its arsenal, is relatively new,” Sarkar said. “While PHP has released patches, enterprises that have deployed PHP-based applications in real-time, especially those with lesser security focus, will be vulnerable.”
Sarkar emphasized the importance of a proactive approach to cybersecurity, stating, “A ready microsegmentation approach, which can deploy containment templates in minutes, is recommended. This will give crucial time to IT leaders to patch vulnerabilities on time.”









