Advanced phishing campaign targets Poland and Germany, delivering Agent Tesla, Snake Keylogger and newly identified TorNet backdoor via .tgz attachments. All by leveraging PureCrypter and TOR network for stealthy C2.
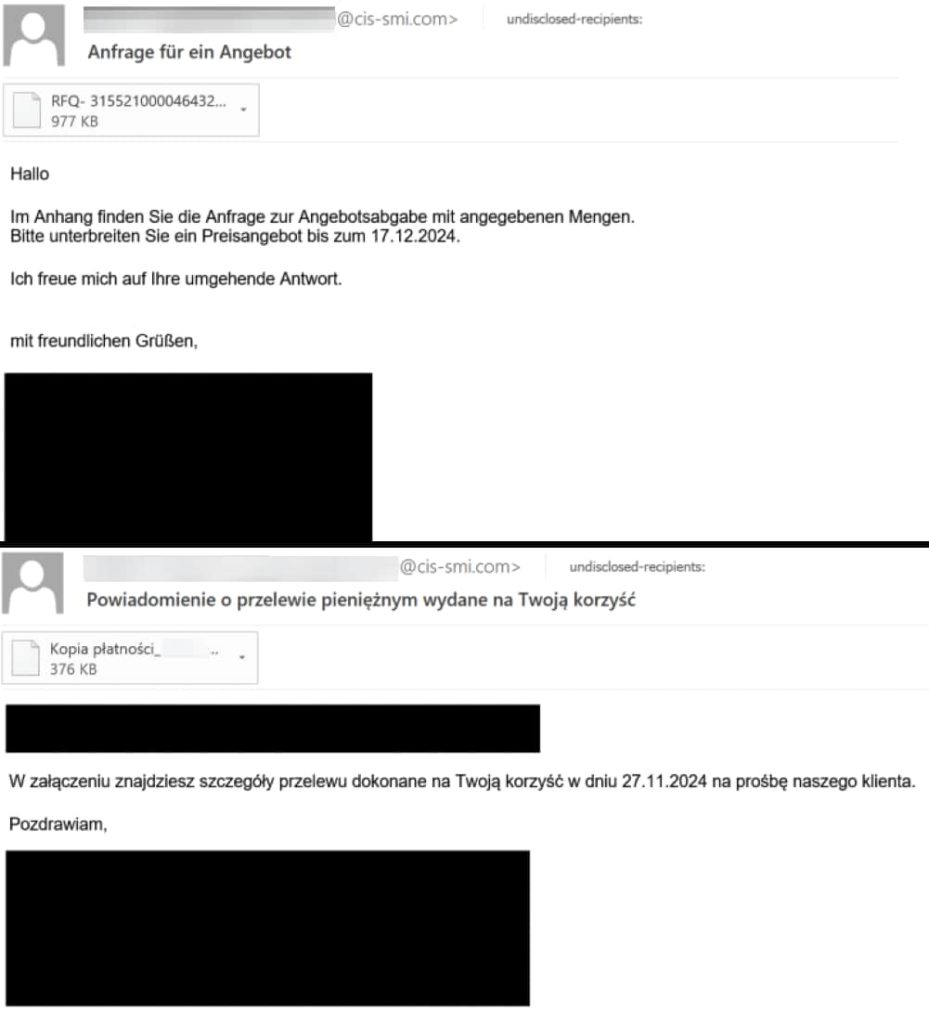
A malicious campaign, discovered by Cisco Talos in July 2024, targeted users primarily in Poland and Germany through phishing emails containing malicious attachments disguised as.tgz files. These emails impersonate financial institutions and businesses, often with themes like money transfer confirmations or order receipts. They are primarily written in Polish and German and contain compressed.tgz files.
According to Cisco Talos’ research, shared with Hackread.com ahead of its publishing on Tuesday 28, the actor has deployed other payloads as well, including “Agent Tesla, Snake Keylogger and a new undocumented backdoor, which researchers dubbed TorNet.
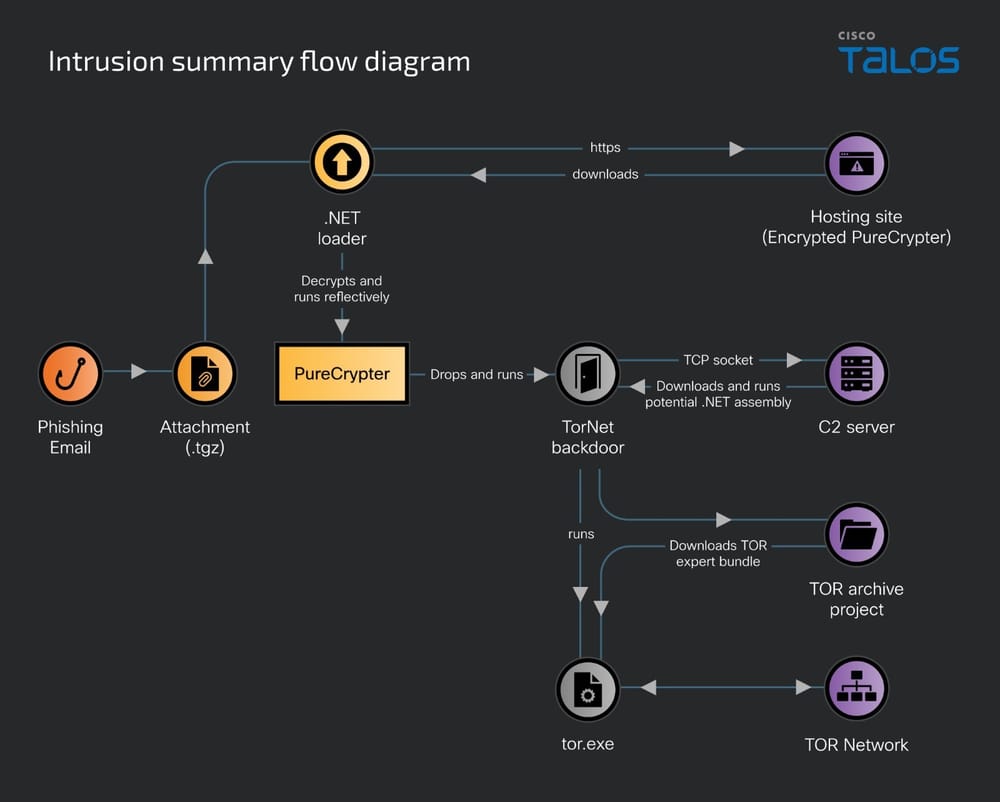
When a user extracts an attachment from a file, a.NET executable file appears, which downloads the next stage of the attack, the PureCrypter malware, from a remote server or within the loader itself (decrypted using the AES algorithm and loaded into the targeted device’s memory).
The PureCrypter malware is a Windows dynamic-link library obfuscated with Eziriz’s.NET Reactor obfuscator. It contains encrypted binaries of legitimate DLLs, including Protobuf-net and Microsoft task scheduler DLL, and the TorNet backdoor.
PureCrypter employs various evasion techniques, including disconnecting the victim’s machine from the network before dropping payloads, checking for a virtual machine, sandbox environment, or debugger status, and modifying Windows Defender settings. It ensures persistence by creating a scheduled task that runs every few minutes, even on low battery, and adding entries to the Windows registry to ensure the loader runs on startup.
Moreover, it drops the TorNet backdoor, which is a relatively new .NET backdoor used in this attack to connect to a C2 server over the TOR network for stealthy communication. It anonymizes the communication with the C2 server, making detection harder. After establishing a connection, it sends identifying information and allows attackers to carry out remote code execution by sending arbitrary.NET assemblies to the C2 server, hence, expanding the attack surface substantially.
The campaign uses advanced techniques like network disconnections, Tor network exploitation, and multi-stage payloads. The use of the Tor network further hinders tracking/disruption. This campaign highlights the need for continuous caution and network monitoring to address attackers’ growing threat tactics.