Beware Macro! Ukrainian users and cyberinfrastructure are being hit by a new malware campaign in which hackers are using a multi-stage malware strategy to deliver the Cobalt Strike.
A recent cyberattack targeting Microsoft Windows-based endpoints in Ukrainian has been discovered by Fortinet’s FortiGuard Labs where attackers leverage a malicious Excel file to deploy Cobalt Strike, a notorious tool used for post-exploitation activities.
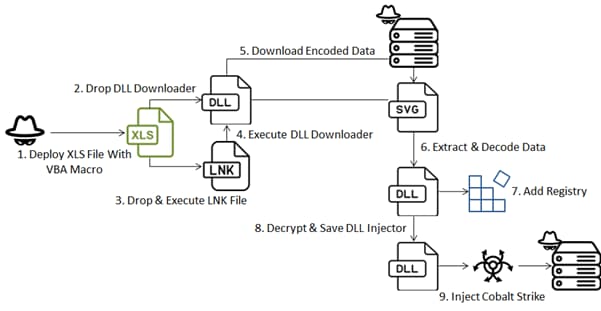
In this attack, an apparently harmless Excel file is embedded with a VBA (Visual Basic for Applications) macro, a scripting language used in Microsoft Office applications. The attacker uses a multi-stage malware strategy to deliver the “Cobalt Strike” payload and establish communication with a command and control server.
The malicious Excel document contains Ukrainian elements to lure users into enabling its macros. The macro deploys a HEX-encoded DLL downloader, which executes the DLL (Dynamic Link Library) file using a shell command.
The DLL file, also disguised as a harmless component, is the key to deploying Cobalt Strike. The downloader examines process names for specific strings related to analysis tools and antivirus software, terminates the program if it detects a matching process, and executes the decoded file using “rundll32.exe”.
As per FortiGuard Labs’s report, The DLL Injector, “ResetEngine.dll,” is responsible for decrypting and injecting the final payload. It uses “NtDelayExecution” to evade detection of malicious activities within sandboxes and then, it decrypts the final payload using an AES algorithm. The code then injects the decrypted data into itself and uses various APIs to execute the final Cobalt Strike.
For your information, Cobalt Strike is a powerful tool that allows attackers to gain a foothold within a compromised system, steal sensitive data, deploy additional malware, and establish network persistence.
Fortinet researchers discovered a geolocation check within the VBA code, ensuring the payload is only downloaded on systems located in Ukraine. This targeted approach indicates a well-orchestrated operation with a specific goal in mind.
This isn’t the first time a malicious Excel file was used to target Ukraine in recent years due to the ongoing geopolitical situation. In 2022, FortiGuard Labs reported a campaign using a malicious Excel document to deliver a Cobalt Strike loader, while Ukraine’s Computer Emergency Response Team confirmed UAC-0057’s involvement in an attack using a malicious XLS file to deploy PicassoLoader and Cobalt Strike Beacon.
This recent attack further highlights the evolving tactics of cybercriminals and the importance of robust cybersecurity measures. Users should be cautious of enabling macros in Excel files, especially from unknown sources and use reliable endpoint security software that can detect and prevent malicious macros.