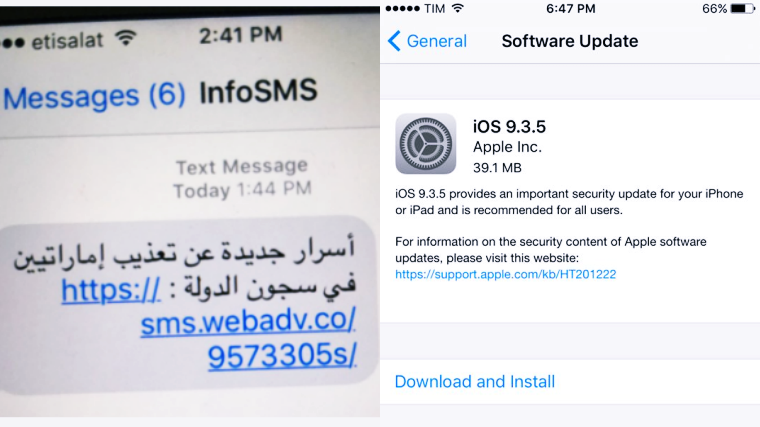
Apple is urging users to update their devices to the latest iOS 9.3.5 in order to protect yourself from a newly found Sophisticated iPhone Spyware.
Apple’s iPhones are always in demand and the preferred choice of gadget-savvy users around the world but, we cannot ignore the fact that iPhone is the most widely attacked smartphone from both individual hackers and government and intelligence networks. On the other hand, Apple Inc. happens to be an extremely well-organized and alert organization when it comes to securing their devices.
According to Citizen Lab and Lookout Security, Apple’s iOS 9 has become the target of a spree of attacks by government-sponsored attackers involving a very advanced malware. Attackers tried to infect the iOS software with a sophisticated spyware to target dissidents and activists. The malware has been dubbed a Pegasus.
The University of Toronto’s Munk School of Global Affairs’ project Citizen Lab is a facility where researchers explore how power is exercised in the digital world to ensure global security. Citizen Lab in collaboration with Lookout Security created a report documenting the entire exploitation feat that was channeled towards iOS 9 devices. According to their analysis, the Stealth Falcon group is behind the attack because this is the group that has been involved in the targeting of internal and external critics of the UAE government. However, Citizen Lab could not identify any active malware that was launched by Stealth Falcon.
Read: Apple Users Hit with Large-Scale Smishing Scam
The company was alerted when Ahmed Mansoor, a renowned human rights activist in UAE received a series of suspicious SMS messages that contained links to sites that offered information about abuses. The messages were forwarded to the Citizen Lab, the firm then collaborated with Lookout Security to observe the malware and this is how the three zero-day vulnerabilities were identified on iOS 9.


Read: Apple Deletes App That Informed Users If Their iPhone is Hacked
It was also observed that the exploiters used these vulnerabilities to exploit iOS 9 devices and triggered a sequence of exploits that involved execution of binary then downloading and installation of the spyware payload. This disabled the automatic updates system fin iOS devices and also removed jailbreaks.
Apple was quick to respond and immediately released an update to its iOS 9 system. The update has been released for the iOS 9.3.5 and it will patch the various zero-day vulnerabilities that have been deployed supposedly by governments. Citizen Lab and Lookout Security informed the iPhone maker about the spyware and the company quickly released the patch, within ten days to be precise.
The research team at Citizen Lab identified the malware when it was sent to a human rights activist based in the Middle East. Apparently, there were three zero-day vulnerabilities about which the independent research firm notified Apple.
It is being suggested that all iOS 9 devices be updated immediately with the new patch because the spyware is quite sophisticated and advanced. If successfully launched, the software hijacks an iOS device so that the attacker could monitor and control it remotely. Then the device’s camera, microphone and audio calls would be intercepted, and this would be possible for conversations made by applications that are secured with end-to-end encryption, such as WhatsApp. Moreover, hijackers can easily steal images, monitor movements of the device owners and retrieve files.
In an interview, Bill Marczak from Citizen Lab stated that “What we have seen from looking at these exploits is that it seems that they have been in the wild a bit longer than the 9.3.3/9.3.4 timeframe.”
As per the representative from Apple the company was identified about this vulnerability and it was immediately fixed with the iOS 9.3.5 patch. The company rep further stated that:
“We advise all of our customers to always download the latest version of iOS to protect themselves against potential security exploits.”
As per Lookout’s VP of Security Research and Response Mike Murray:
“The … vulnerability chain is the first that anyone’s seen of a one-click remote jailbreak of an Apple device. It’s the smoking gun active mobile threat that we’ve always known existed but didn’t yet have proof of. This demonstrates that highly resourced actors see the mobile platform as a fertile target for gathering information about targets and regularly exploit the mobile environment for this purpose.”
It must be noted that zero-day exploits are relatively common on iOS devices because governments can easily exploit any prevailing flaws in the iOS system. Such flaws, if identified by an attacker, can easily be sold to governments for quite an enormous amount, approx. $500,000 to $1 million.
This would probably be the very first time when such a major attack has been identified and countered at such a quick pace. According to Marczak, Citizen Lab has been trying to track down the perpetrators of this attack from quite some time and then the breakthrough occurred when an activist sent them phishing links, which matched the domain that the research firm was following already.
Read: Cop Exploited iPhone App to Secretly Watch Mom Breastfeeding
The reason why Apple is urging the users of iOS 9 to update their devices at the earliest opportunity is that out-of-date devices are now vulnerable to the attack, which Marczak has identified to be a “fairly sophisticated exploit.”
According to Citizen Lab, this is the most “sophisticated spyware” one-click remote jailbreaking zero-day vulnerability. Therefore users of iOS version 9.3.4 or below must update their devices with the patch iOS v9.3.5.