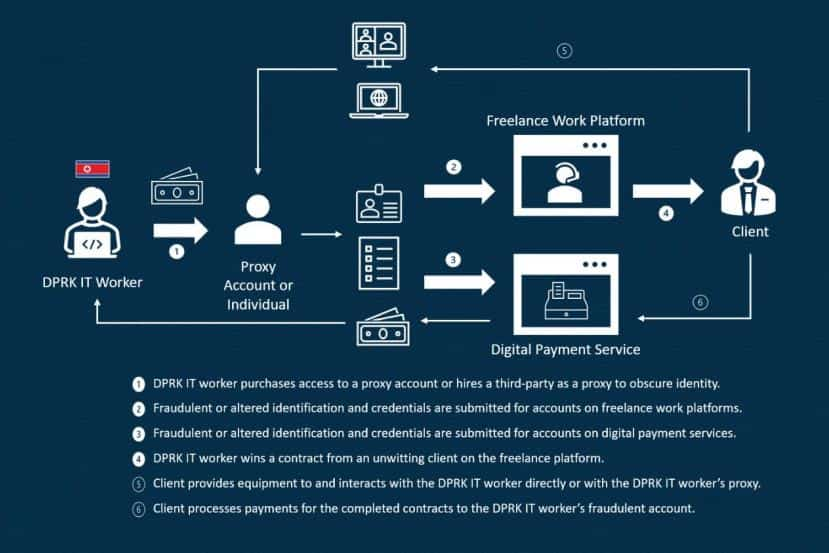
The US government has warned organizations to beware of North Korean hackers in the guise of IT freelancers claiming to be non-DPRK (Democratic People’s Republic of Korea) nationals.
According to an advisory issued by the United States State and Treasury Departments and the Federal Bureau of Investigation (FBI), highly skilled mobile app and software developers from North Korea are trying to get employed by posing as IT freelancers.
The advisory stated that the purpose behind this fraudulent activity is to pave the way for cyber intrusions from the North Korean government. The fraudsters hide their identities and locations by using VPNs and pose to hail from another country to gain employers’ trust.
Nefarious Objectives of North Korean IT Experts Exposed
The joint advisory published (PDF) on Monday revealed that the primary objective behind this scam is to generate revenue for the North Korean government to circumvent sanctions and carry out a cyber invasion. The IT experts from North Korea exploit the growing demand for remote work to get freelance employment contracts without revealing their true identities.
The key targets are organizations in the USA, East Asia, and Europe, and most imposters were situated in Russia, China, Africa, and Southeast Asia. This scam indicates North Korea’s realization that IT skills are highly demanded in the abovementioned regions.
What Happens After Employment?
After getting employed, the North Korean hackers generate a ‘critical stream’ of revenue to ensure the North Korean government receives funding for its activities and supports their supreme leader Kim Jong Un.
According to authorities, most of the individuals are working on behalf of entities that were directly hit or were involved in North Korea’s WMD and ballistic missile programs, “as well as its advanced conventional weapons development and trade sectors.” For your information, these programs are prohibited by the UN.
Possible Dangers
The US government believes North Korean IT workers appear to engage in routine IT work. They use privileged access to fulfil their country’s malicious objectives. The advisory noted that some of these workers provided logistical aid to cybercriminals in North Korea.
Furthermore, they share access to the US firms’ virtual infrastructure and helped sell data stolen by North Korean threat actors. They also assist them in money laundering and virtual money transactions.
The advisory stated that hiring North Korean hackers can have far-reaching consequences as it may lead to legal and reputational losses, such as sanctions imposed under the US and UN authorities.
How to Detect Fraudsters?
The advisory offered guidelines on identifying hackers posing as IT workers by providing potential red flags that should raise concerns. Organizations should check the workers’ activities by including multiple logins into an account that uses different IP addresses within a short time. Another strategy would be to check technical configurations linked to the desktop sharing software, router port, and account login frequency.
RELATED TOPICS
- Feds Bust N. Korean Identity Theft Ring Targeting US Firms
- Hackers used fake job website to scam jobless US veterans
- Fake LinkedIn job offers scam spreading More_eggs backdoor
- Fake GitHub Repos Caught Dropping Malware as PoCs AGAIN!
- Employee Duped by AI-Generated CFO in $25.6M Deepfake Scam
- Fake PoC Script Tricked Researchers into Downloading VenomRAT