A sophisticated ValleyRAT campaign is targeting Chinese Windows users. Learn about the malware’s multi-stage attack, its ability to evade detection, and the potential impact on compromised systems. Understand the threat actor’s tactics and the risks posed to individuals and organizations.
A new research report from FortiGuard Labs exposes a sophisticated campaign specifically targeting Chinese Windows users with ValleyRAT malware. This is a multi-stage malware targeting e-commerce, finance, sales, and management enterprises.
Initial Infection:
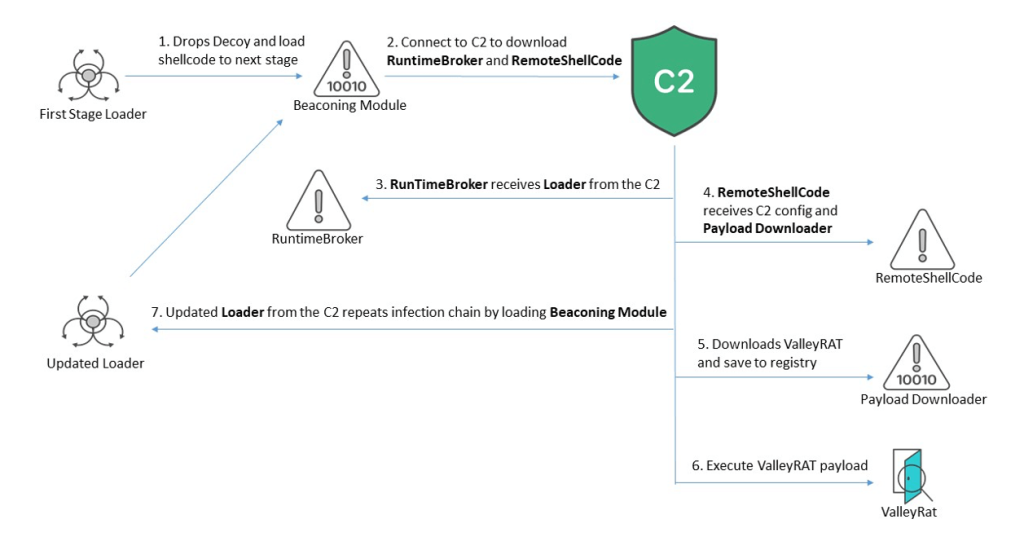
The attack begins with a deceptive lure, often disguised as a legitimate document related to finance or business, using icons of legitimate applications, like Microsoft Office. It creates an empty file and executes the default application for opening Microsoft Office Word documents.
If no default application is set, it displays an error message. Once executed, the malware establishes persistence on the system by creating a mutex and modifying registry entries. It also attempts to evade detection by checking for virtual environments and employing obfuscation techniques.
Payload Delivery and Execution:
A key element of this attack is the use of shellcode. This allows the malware to load its components directly into memory, bypassing traditional file-based detection methods. The malware then communicates with a command-and-control (C2) server to download additional components, including the core ValleyRAT payload.
According to FortiGuard Labs’ blog post shared with Hackread.com ahead of publication on Thursday, ValleyRAT malware is attributed to the suspected APT group “Silver Fox.” It focuses on graphically monitoring user activities and delivering plugins and malware to the victim system.
Evasion Techniques:
To increase its chances of success, the malware employs several evasion tactics. These include disabling antivirus software, modifying registry settings to hinder security applications, and using sleep obfuscation to hinder analysis, evade memory scanners and encode its shellcode with an XOR operation.
Payload Capabilities:
The core ValleyRAT payload grants attackers extensive control over the compromised system. Once in the system, it supports commands to monitor activities and deliver arbitrary plugins to further the threat actors’ intentions.
Additionally, ValleyRAT monitors user activity, steals data, and potentially deploys additional malicious payloads. It accomplishes this through a series of commands, including the capability to load plugins, capture screenshots, execute files, manipulate the registry, and control system functions like restarts, shutdowns, and logoffs.
The campaign’s targeting of Chinese users is evident in its use of Chinese-language lures and its focus on evading popular Chinese antivirus products. The malware’s persistence and ability to execute commands remotely make it a significant threat to affected systems.
This is an evolving campaign. Hackread.com will update readers regarding any new findings. Meanwhile, users are advised to maintain updated security software and exercise caution when opening unexpected files or links.