Morphisec uncovers a new ValleyRAT malware variant with advanced evasion tactics, multi-stage infection chains, and novel delivery methods targeting systems.
Cybersecurity researchers at Morphisec Threat Lab have discovered a new version of the sophisticated ValleyRAT malware distributed through various channels including phishing emails, instant messaging platforms and compromised websites. ValleyRAT is a multi-stage malware, linked to the notorious Silver Fox APT group.
According to Morphisec’s investigation, shared with Hackread.com, the key targets of this campaign are high-value individuals within organizations, especially those in finance, accounting, and sales, and the objective is to steal sensitive data.
Earlier ValleyRAT versions utilized PowerShell scripts disguised as legitimate software installers, which often employed DLL hijacking to inject their payload into signed executables from programs like WPS Office and even Firefox. In August 2024, Hackread.com reported about a ValleyRAT version using shellcode to inject malware components directly into the memory.
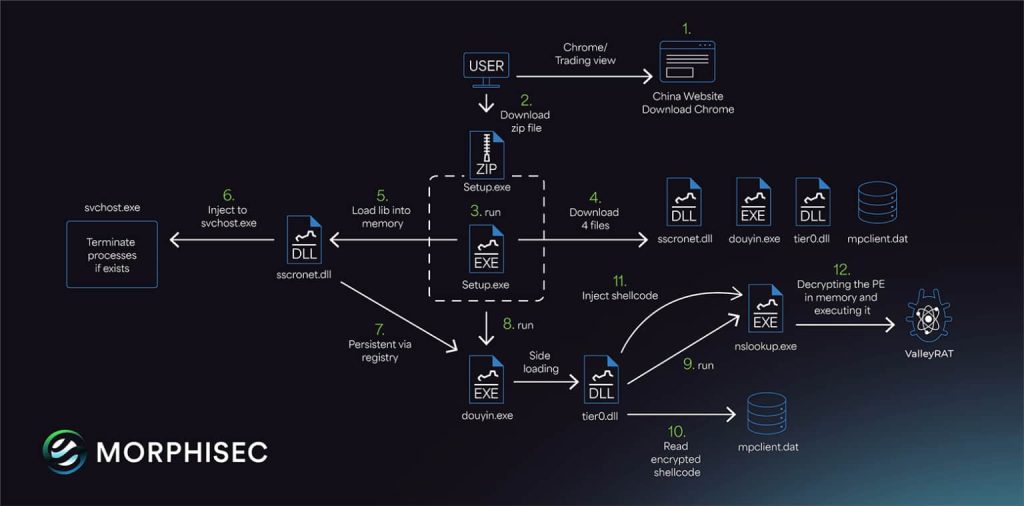
Conversely, the current version uses a fake Chinese telecom company “Karlos” website (karlostclub/) to distribute the malware, which downloads a series of files, including a .NET executable that checks for administrator privileges and downloads additional components, including a DLL file.
“Interestingly, the actor reused the same URL for both the older and newer versions of their attack,” researchers wrote in the blog post.
According to researchers, a fake Chrome browser download from anizomcom/ is the initial infection vector in the attack chain, tricking the victim into downloading and executing the malware. The sscronet.dll file, deliberately named with a legitimate-sounding identifier to avoid suspicion, injects code into the legitimate svchost.exe process, acting as a monitor, terminating any processes on a predefined exclusion list to prevent interference with the malware’s operation.
Next, the malware utilizes a modified version of the Douyin (Chinese TikTok) executable for DLL side-loading and a legitimate Tier0.dll from Valve games (specifically Left 4 Dead 2 and Killing Floor 2) to execute code hidden within the nslookup.exe process. This process retrieves and decrypts the main ValleyRAT payload from mpclient.dat.
The decrypted payload uses the Donut shellcode to execute the malware in memory, bypassing traditional disk-based detection methods. It also tries to disable security mechanisms like AMSI and ETW.
For your information, ValleyRAT is a C++-based remote access trojan with basic RAT functionalities such as accessing the WinSta0 window station for screen, keyboard, and mouse interaction and monitoring the victim’s screen. It incorporates extensive anti-VMware checks to evade detection in virtualized environments and connects with its C2 server using IP addresses and ports that are initialized within its code during installation.
“If the malware does not detect that it is running inside a virtual machine (VM), it attempts to establish a connection to baidu.com as part of its network communication check,” researchers noted.
The Silver Fox APT group’s changing tactics/evasion techniques show the growing sophistication of new attacks. Organizations should adopt a proper security strategy, including stricter endpoint protection, employee training, and continuous monitoring, to mitigate risks.










