Meet XKeyscore a tool used by NSA which can track and store everything a user does through the internet — XKeyscore allows the collection of the widest range of data that is served online — The analysts working for NSA need no pre-approval for conducting any searches — Sweeps all the browsing history, activities in social media and emails.
XKeyscore is tool of the NSA which allows this gigantic security agency to gain access and to sweep through huge databases of online data which contains chat history, email and other browsing history of the global internet users, says the documents which have been released by the Whistleblower Snowden.
NSA boasts that the XKeyscore tool that they have made is a program that allows them to acquire the widest range of online data for intelligence and surveillance purposes.
The recent intense debates that have been carried out by the people and the congress related to the reach or the extent to which the surveillance programs of NSA can go will give rise to new revelations as the senior authorities of the agency will show different documents to the senate judiciary committee on Wednesday. The documents will be shown as a response to stories have been published in the media related to the phone records that the agency collects.
The files throw light on the controversial statements that have been made by Snowden in the first video interview that was published and released by Guardian back on June 10.
Snowden said in his interview that I can easily wiretap anyone whatsoever buy just sitting on my desk. US officials have however denied the statement that Snowden has made and have replied that this is impossible and he cannot make this statement true as he is just telling a lie.
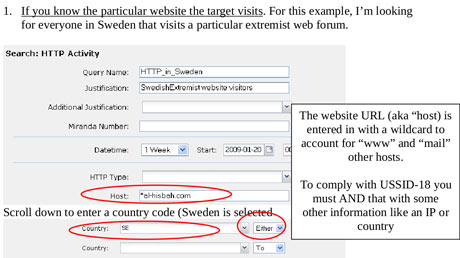
But the training material for the XKeyscore program have rendered details about how this program can enable one to gain access to a large number of databases that the agency has and this can be done by simply filling in a form on which you only need to give a broad reason or justification for carrying out the search. The request for the search is neither reviewed by any of the officials of the NSA or neither the court and is processed for execution.
The documents states that XKeyscore is a intelligence tool which is the most far reaching intelligence system which develops intelligence from networks of computers and this intelligence network has been termed by the agency as Digital Network intelligence. One of the presentation claims that his intelligence programs enables the coverage of all the activities that a typical user of the internet performs and includes chat histories, emails, searches made, websites visited and even the metadata.
Analysts at NSDA also have the ability to intercept and interpret the real time activities that re being carried out by any individual on the internet and this is performed by using either the XKeyscore or by using other intelligence programs that they have developed.
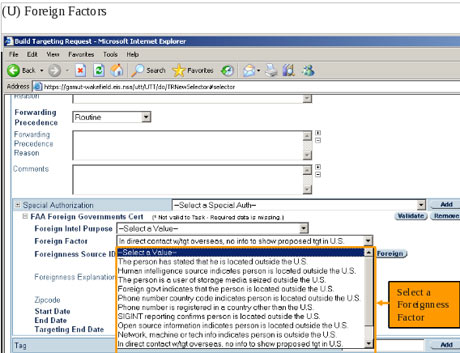
If you go with the US law, NSA should first obtain an individualized Fisa warrant in case the targeted person for surveillance is a civilian of the US but no such permission or warrant is required to be taken if any such person is interacting with a foreign target. XKeyscore though does not give the legal authority but gives the capability to an analyst to track the activities of any US person if the analyst has some sort of identification such as IP address or email of the person being targeted for an extensive surveillance.
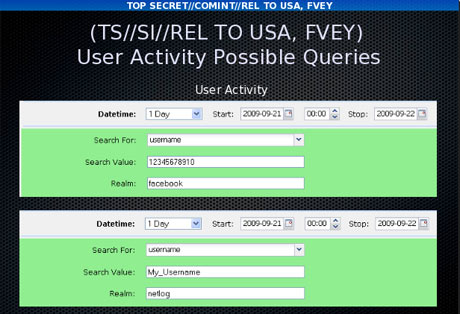
A training slide also shows that XKeyscore constantly gathers the details of the digital activities going on and the NSA analyst can conduct query with the database at will.
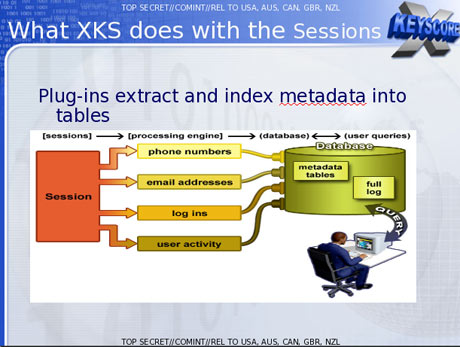
The purpose behind XKeyscore is to collect and search out all the metadata along with the other online information such as email accounts, browsing and search history, chat history etc. and the program can do this even without having any knowledge about the email account of the person that is being targeted for surveillance.
Analysts also have the leverage to conduct a search using keywords, IP address, telephone number and the language in which an activity was conducted on the internet. They can also make the search based on the type of the browser that has been used in browsing.
One of the documents notifies that the use of so many methods for carrying out the search is due to the reason that searching information through using email account limits the ability to track all the activities because when a person is using the internet, he activities performed are quite anonymous or you can say that not all the activities performed will be through an email account.
Documents of NSA have revealed that around 300 different terrorists have been arrested till the year 2008 using the XKeyscore program.
The analysts have been warned that the search of the complete databases that they have will yield a large number of results which are difficult to go through and most of them might be irrelevant. The have been advised to also use the metadata which has been stored on the databases and which cuts down the results and makes it more specific at what data should be reviewed.
A slide with a title ‘’plugin’’ which was released in December 2012 has indicated the different items or the fields that can be searched in the program and includes emails that are checked in a session both by domain and username. Similarly the phone numbers are also checked in a session via entries of the address book and the signature block. The other field or the information that is searched is the emails and the chat history which include cookies that are machine specific and the buddy list.
Monitoring of emails
In his second interview with the Guardian, Snowden briefed out and explained how he can gain access and read all the emails of a person if he only has the person’s email address. He also said that the claim which he has made is partly based on the capability of the XKeyscore program to search out the emails and Snowden also said that he had the authority to do so while he was working for the NSA.
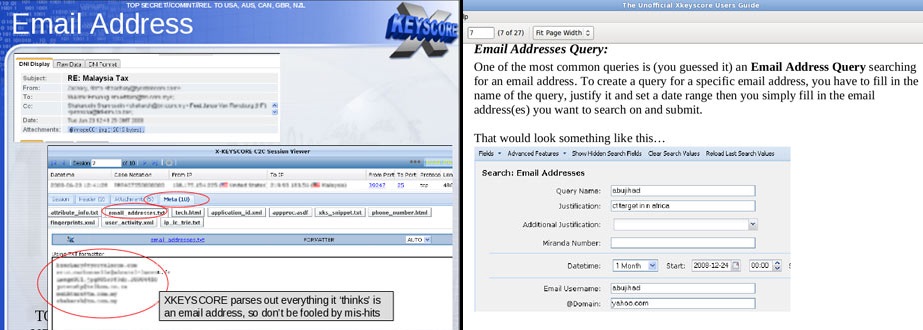
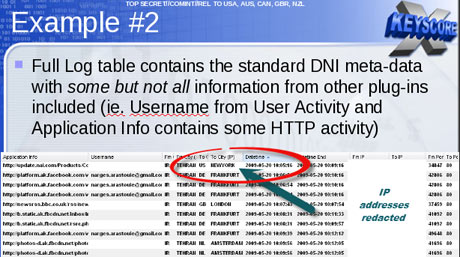
A confidential documents gives out all the details about how the programs conducts searched through the bodies of web pages, emails and other documents and includes the email particulars such as TO, BCC, CC, From and the pages of Contact us.
To access the mail account of an individual, the analyst only requires to enter the email address of the targeted person and will on enter a justification for doing the same along with the sorting time for searching the emails of the person. The emails which are then accessed will be selected by the analyst to open and to read them in a software of the NSA.
The system is quite similar to the manner in which the analysts at the NSA intercepts various online communications that transit through the USA or which are terminated in the USA.
A top secret document released in 2010 describes how the analysts at the NSA are trained for conducting general surveillance under FISA act and explains that the analysts can conduct surveillance on any person by simply using some pull down menus which they have devised for gaining both targeting and legal justifications. After just selecting the different options that appear on the pull-down menus in the programs, an electronic surveillance of the targets is conducted and it gives the analysts the ability to review all the communication content.
Browsing, chat history and other activities
A part from the emails data, XKeyscore allows an analyst to track a wide array of other online information and activities and includes those activities that are conducted through the use
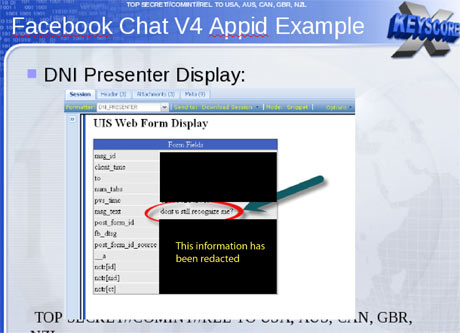
of social media. The DNI presenter which a tool of the NSA used to read the stored email content also allows an analyst to read the social media data such as private messages or Facebook chat. A Facebook chat of a person can be read by the analyst by just entering the user name of the person and the date range for which the chat data needs to be sorted out.
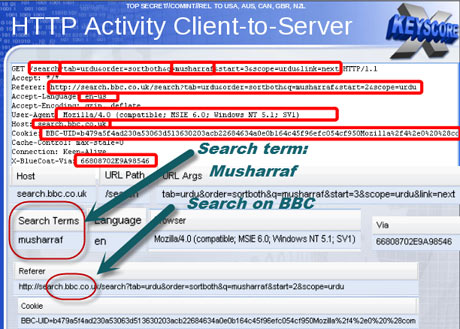
They can track the browsing activities of a user using a wide spectrum of different search information and this includes the search terms that have been used by the user and the websites that a user has visited.
A slide has also indicated the HTTP search ability of the program using the keyboard and this search ability allows an analyst to tracks almost all the activities that are done by a typical user via the internet. The XKeyscore programs also enables an analyst to track out the IP address of any user who has visited a website and for this purpose, the analyst only has to give the program the website that the user has visited.
The amount of the communications or the activities that can be tracked through the XKeyscore program is massive and a report of NSA from 2007 shows that there have been around 850 billion call events that have been tracked and stored on the databases of NSA and similarly there have been 150 billion internet records that have been tracked and stored. The documents also stated that 1-2 billion record are added to the databases on a daily basis.
An article from the Washington Post which was published back in 2010 said that there are about 1.7 billion phone calls, emails and other communication records that are tracked by the NSA program and are stored onto their databases.
The XKeyscore program of the NSA collects such a huge amount of data that it can be stored for a long terms and is only kept for about 4 to 5 days before it is updated. However, the metadata that they collect is stored on their databases for about 30 days. One of the documents says that’ ‘’on some of the websites, we receive a data which is about 20 terabytes and it can be stored for only about 24 hours’’.
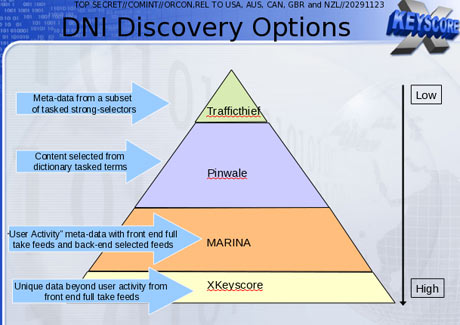
To solve his issue or limitation, NSA has devised a multi-tiered system in which the analyst can store the data that they find interesting or relevant to what they are looking out for. One of such database is termed as Pinwale and this database can store the data for around 5 years.
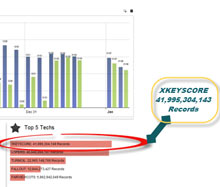
A document also shows that it is the XKeyscore database which contained the largest amount of data which has been tracked and stored by NSA.
In the year 2012, a data of 41 billion cords has been stored on the XKeyscore program and this data was only gathered via a 30day surveillance.
Technical versus Legal restrictions
Though a warrant is required according to the FISA act for targeting a UIS person, but no such warrant will be needed if the US person is in any sort of contact with a foreign person who is a target of the NSA.
Jameel Jaffer who is a deputy director of the ACLU told the guardian that the officials of the NSA have said that this new line has been framed to allow the NSA to keep track on the activities of the US person without having to acquire an individualized warrant.
Jameel Jaffer also said that the government is no need to target any of the US persons because when they inevitably intercept a large amount of communication of the American people in the process of targeting foreign targets.
A XKeyscore document has rendered an example of an American target in Tehran which was communicating with the US people in Amsterdam, New York and in Frankfurt.
In the recent times, NSA has made an attempt to bifurcate the US domestic communication in different databases that they have devised for this very purpose. Having said that, the documents of NSA have indicated that this attempt is quite imperfect because even the domestic communications have a tendency to run on to the foreign systems and the tools that NSA is using is sometimes unable to identify the origin of the national communication.
Moreover the information or the communication that takes place between a US person and a foreign target are stored on the same database on which the foreign to foreign communication is stored. This allows the analyst to search out any information of any US person on the database without any individualized warrant.
The searches that are made by the analysts of the NSA are periodically reviewed by some supervisors that also belong to the NSA. Snowden told the guardian in 2010 that we are not normally questioned on what searches we make and even if a question is asked, it is just bulk up a justification for the same.
In a letter which was sent by James Clapper who is the director of NSA to the senator Ron Wyden, he has acknowledged that the legal limitation that have been imposed on NSA for domestic surveillance have been violated by them in their domestic surveillance operations.
Clapper has termed the compliance problems as the human errors which is due to the sophisticated technology and not due to any bad Faith.
However senator Wyden on Tuesday has said on the floor of the senate that these violations are far more serious than those which have been told by the intelligence community and are quite troubling.
NSA gave a statement that the surveillance program or the tracking of information that they make is only catered to target the foreign targets and they need to do so to meet the requirements that their leaders need to effectively safeguard the interest of the country and to protect this nation. They also said the XKeyscore program of NSA is a lawful program of the foreign signal collection which is designed for intelligence and surveillance on foreign threats.
They have also said that the allegations which say that there is no control check on the analysts for collecting and accessing widespread information is not true at all. Access to XKeyscore for any surveillance purpose is only given to the officials who needs such access to perform the tasks that they have been assigned. There are many technical, supervisory and manual checks that they have designed within the system and these checks enable to prevent any sort of mishandling or miss-use of any data or information.
Every search that is made by any analyst on NSA is auditable and answerable and is checked to ensure that such searches are made in line with the rules and regulations and are under proper justification.
These types of programs that we have devised are only for the purpose of allowing us to collect the information and the data which are mandatory for us to perform our various missions effectively. They are to enable us to protect the interest of our people and the sovereignty of our country and to protect the interest of the allied nations that we have.