CloudSEK uncovers a Zendesk vulnerability allowing cybercriminals to exploit subdomains for phishing and investment scams. Learn about the risks and needed fixes.
Cybersecurity researchers at CloudSEK have identified a security vulnerability in Zendesk’s SaaS platform. The platform’s subdomain registration feature can be exploited by cybercriminals to launch phishing and investment scams.
Zendesk, a widely-used customer support platform, offers free trial accounts and allows users to easily register subdomains. According to CloudSEK’s analysis, this functionality can be abused by threat actors to create subdomains resembling legitimate brands, enabling convincing phishing campaigns.
Researchers noted that the vulnerability could be exploited in “pig butchering” scams, a form of investment fraud where victims are groomed over time into investing in fraudulent schemes.
CloudSEK’s analysis found 1,912 instances of Zendesk websites since 2023, with some companies showing an unusually high number of registered subdomains. While intended to facilitate rapid business setup, this feature introduces a significant security risk.
Attackers can use Zendesk’s platform to create fake subdomains, launch phishing campaigns, and build trust through its professional appearance. Leveraging Zendesk’s communication features, they can send phishing emails disguised as legitimate customer support messages. These emails often include malicious links or attachments to lure victims into clicking.
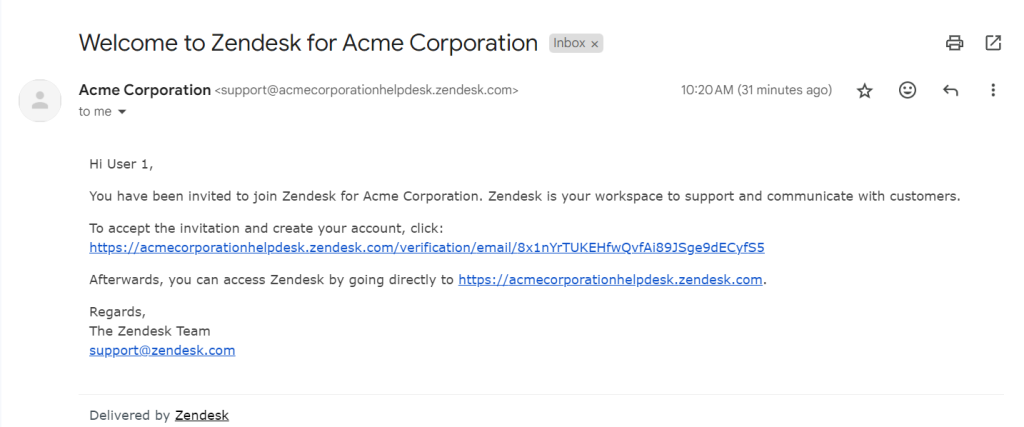
In one demo phishing attack against XYZ Company, an attacker registered a URL mimicking the target company’s address, provided email, name, and company size details, and named a Zendesk instance. They then registered a subdomain, obtained admin access, and sent an invitation email. Threat actors used this setup to link active phishing pages to users, pretending to assign tickets.
Malicious links within the emails redirected victims to fake investment platforms or support pages controlled by the attackers. These platforms were designed to manipulate victims into sharing sensitive information or transferring funds.
CloudSEK’s research shared with Hackread.com also points out a critical flaw in Zendesk’s email validation process. The platform lacks essential checks when adding users to subdomains, allowing attackers to target employees and customers with phishing attempts disguised as legitimate ticket assignments. Zendesk emails often land directly in users’ primary inboxes, increasing the likelihood of interaction.
CloudSEK responsibly disclosed the vulnerability to Zendesk, urging prompt action to mitigate its exploitation by cybercriminals.