DeepSeek, a Chinese AI company, has made a name for itself with its AI models that rival OpenAI’s systems. But along with its rise came a serious security issue as researchers at Wiz found that a database tied to the company was left publicly accessible, exposing over a million log entries, backend details, software keys, and more.
How It Happened
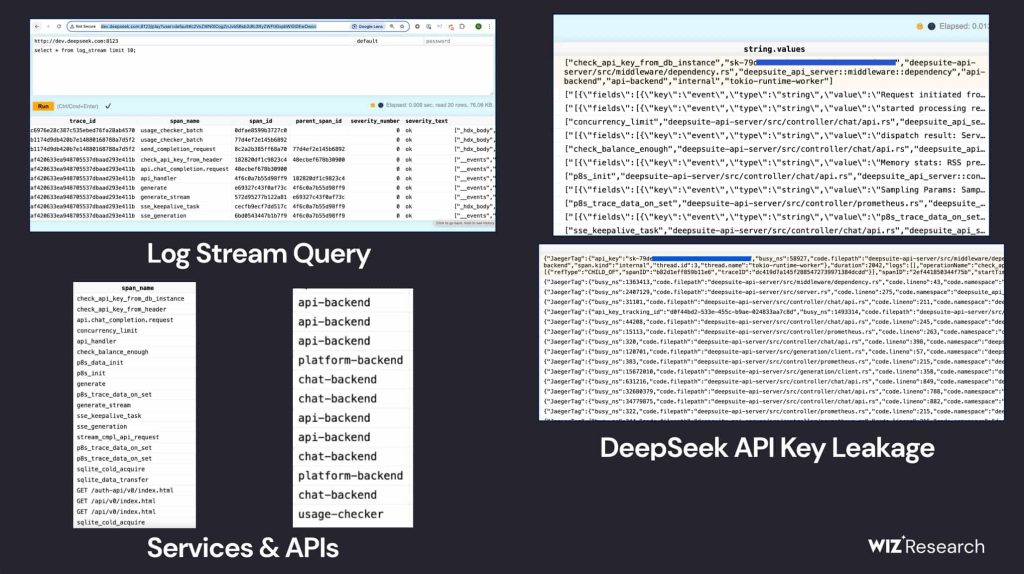
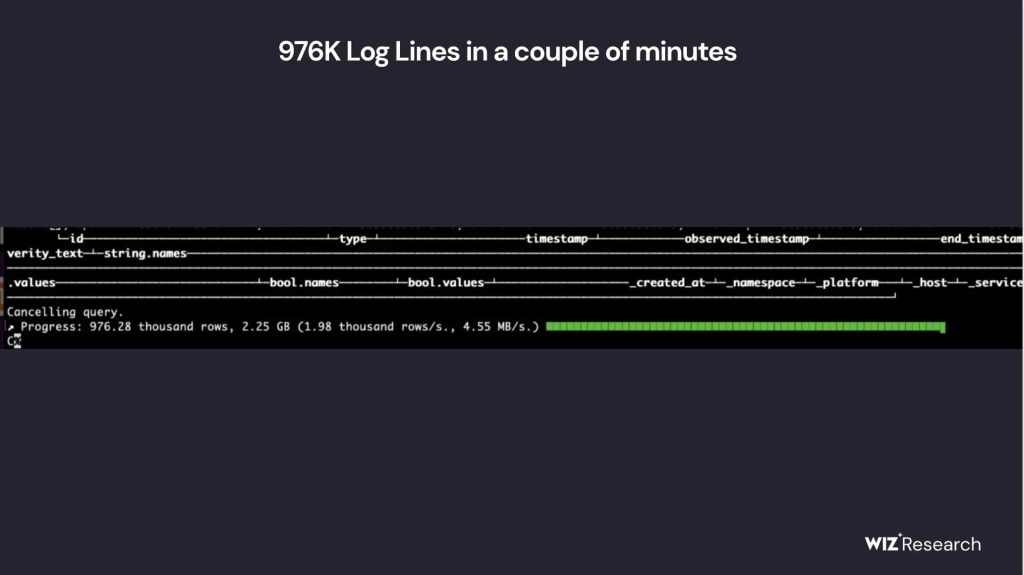
During a routine security assessment, researchers at Wiz discovered that DeepSeek had an unprotected ClickHouse database, open to anyone with internet access. This database wasn’t just visible; it allowed full control over stored data, meaning an attacker could manipulate or extract critical information without restriction.
The exposed database was linked to multiple subdomains, including:
dev.deepseek.com:9000
oauth2callback.deepseek.com:9000
ClickHouse is an open-source, columnar database management system designed to process analytical queries on large datasets quickly. Originally developed by Yandex, it’s widely used for real-time data analytics, log processing, and business intelligence.
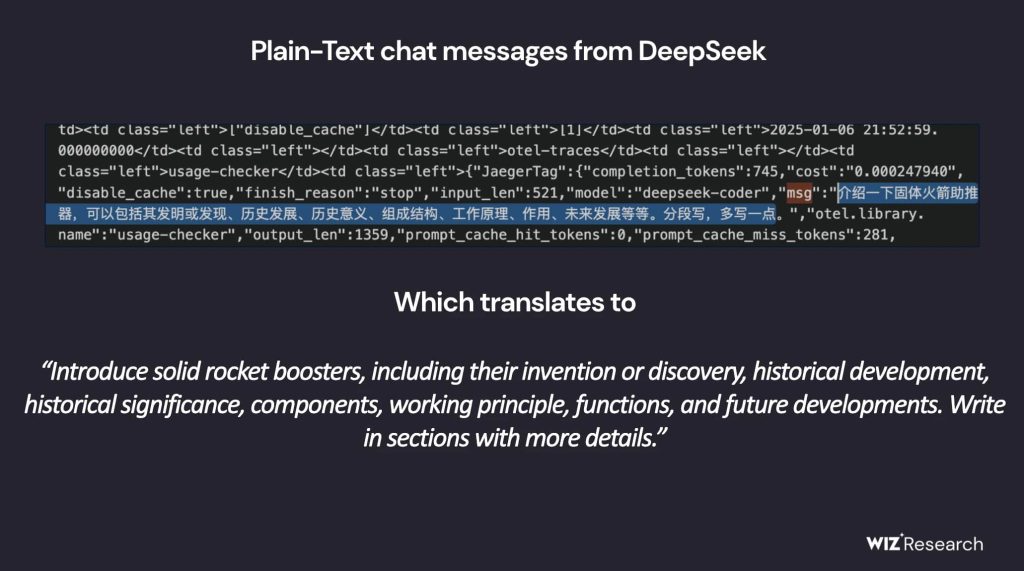
According to Wiz’s blog post, its researchers were able to query the system without authentication, revealing a massive volume of logs containing:
- API keys
- Chat histories
- Backend service details
- System operational metadata
This wasn’t just a minor misconfiguration. The database contained detailed logs of internal system activity, exposing how DeepSeek’s AI tools operate and communicate. Worse yet, the exposure meant attackers could execute commands and extract even more sensitive data directly from the server.
What Was at Risk?
DeepSeek’s AI services process large amounts of user-generated data, meaning chat logs could have included personal or proprietary information. The database also stored API keys, which, in the wrong hands, could allow attackers to impersonate DeepSeek’s services or access further internal systems.
Given the expansion of AI startups, security often takes a backseat to development speed. In this case, a simple security lapse exposed valuable internal data, which could have been exploited by cybercriminals.
DeepSeek’s Response
Once notified by Wiz, DeepSeek moved quickly to lock down the database and remove public access. However, it remains unclear whether any unauthorized parties accessed the information before it was secured.
DeepSeek: Privacy and Cybersecurity Concerns
DeepSeek’s Chinese ownership has already raised concerns among Western governments, with some critics arguing that the chatbot collects excessive personal data, posing privacy risks. Adding to these worries, DeepSeek recently reported a “large malicious attack” that forced the company to suspend new user registrations. Now, with a publicly exposed database compromising sensitive information, the company faces yet another cybersecurity setback.
Expert Opinion
Gunter Ollmann, CTO at Cobalt, notes that situations like the DeepSeek issue happen often because the process of getting the product up and running takes priority over security. Also, since DeepSeek has taken a prominent place in the world of AI, the impact could have been huge for companies and individual users.
“The DeepSeek exposure highlights a critical and recurring issue—organizations, especially those innovating rapidly in AI, often prioritize speed over security.” Explained Gunter. “Wiz’s discovery reinforces the importance of proactive security testing, particularly as attack surfaces expand with cloud-based infrastructure and publicly accessible APIs.”