Cybersecurity researchers at Trend Micro are warning about a new scam where cybercriminals pose as tech support to gain access to victims’ computers. But this isn’t just another spam email scheme; attackers are flooding inboxes and even reaching out through Microsoft Teams to trick people into letting them in. Once inside, they deploy ransomware from groups like Black Basta and Cactus.
Here’s how it works:
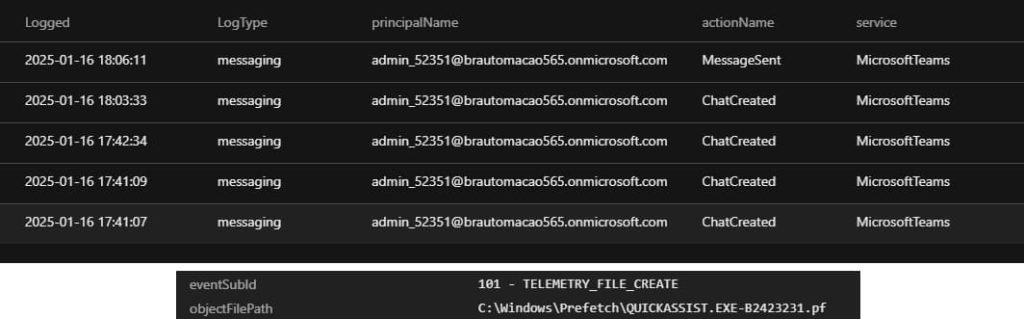
Victims first get bombarded with a flood of emails. Shortly after, someone claiming to be from the IT department contacts them through Microsoft Teams or even a phone call. This “helper” then convinces the user to grant them remote access to their computer, often using a legitimate program called Quick Assist, which is built into Windows to allow remote tech support.
Once inside, the scammer downloads files that seem harmless at first but are secretly combined and unpacked to install a backdoor called BackConnect. Hidden in OneDrive, this backdoor gives attackers full control over the infected system.
It’s worth noting that the Black Basta gang was previously flagged in December 2024 for a similar modus operandi, using email bombing to target Microsoft Teams users. However, at that time, the group was deploying Zbot and DarkGate malware instead.
According to Trend Micro’s latest technical report, recent incidents analyzed by the company show a strong connection between this BackConnect malware and the notorious Black Basta ransomware group, which reportedly made over $100 million from victims in 2023. There’s even evidence suggesting some members of Black Basta have moved over to another ransomware gang called Cactus, as the methods used in recent Cactus attacks are strikingly similar.
These attacks have been particularly active since October 2024, primarily hitting organizations in North America, with the United States suffering the most. The manufacturing sector, followed by finance, investment consulting, and real estate, have been frequent targets for Black Basta.
In some cases, after establishing their backdoor, attackers have been seen using more advanced methods to spread through a network, even targeting specialized systems like ESXi hosts used for running virtual machines. They use tools like WinSCP to move files around and have been caught preparing to encrypt files before being stopped. Leaked internal chats from Black Basta reveal the group sees security tools like Trend Micro as a significant hurdle, showing they are actively trying to find ways around them.
BlackBasta’s internal chats just got exposed, proving once again that cybercriminals are their own worst enemies. Keep burning our intelligence sources, we don’t mind. 😉 pic.twitter.com/6So7dl7xXn
— PRODAFT (@PRODAFT) February 20, 2025
What makes these attacks effective is not necessarily the complexity of the software used, but the way attackers manipulate people. By mixing social engineering with the abuse of genuine software and cloud services, they make their malicious actions look like normal computer activity. It highlights that cybersecurity isn’t just about having the right software, but also about being aware of how criminals try to deceive people.
What You Should and Should NOT Do!
If you’re a Microsoft Teams user, don’t panic if you suddenly get flooded with emails. Instead, contact your system administrator to ensure these emails are blocked immediately and your device is scanned regularly. Report any suspicious emails or calls from unknown third parties posing as “helpers” to your cybersecurity team.
Remember, you don’t need a helper if you never asked for one; especially when the ‘helper’ is the one who caused the problem in the first place.