Fake browser update scams now target Mac, Windows, and Android users, delivering malware like FrigidStealer, Lumma Stealer, and Marcher trojan through compromised websites.
Cybersecurity researchers at Proofpoint have identified two new cybercriminal groups behind a wave of fake browser update scams designed to infect users with malware. These groups, tracked as TA2726 and TA2727, are using compromised websites to trick visitors into downloading malicious software with now including a newly discovered Mac-specific information stealer called FrigidStealer.
How the Attack Works
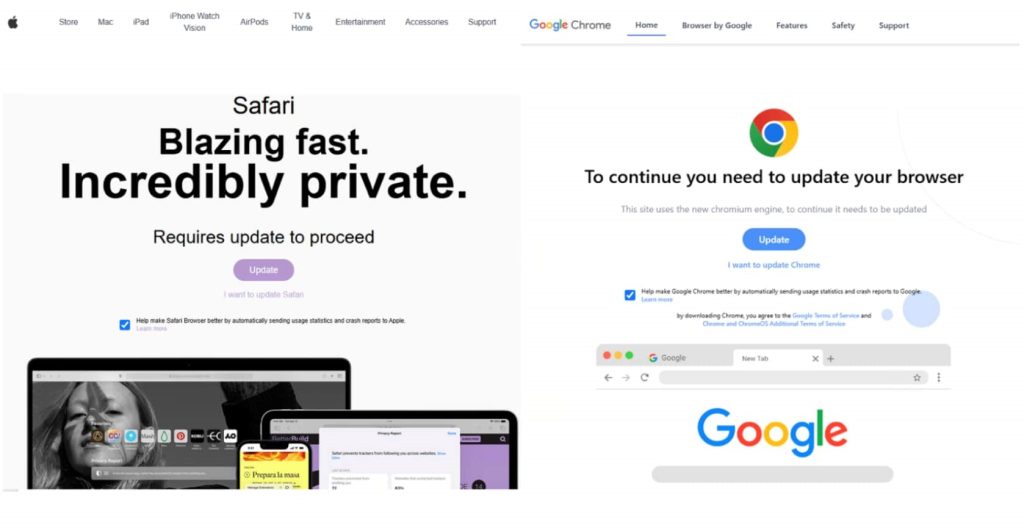
The scam relies on web injects, a technique where attackers insert malicious code into legitimate websites. When users visit an infected site, they see a fake browser update prompt urging them to download and install an update. Instead of a real update, the download delivers malware that can steal sensitive data or install more dangerous payloads.
TA2726 and TA2727
TA2726 operates as a traffic seller, essentially providing this redirection service for other malicious actors. Researchers believe that TA2726 appears to be working alongside TA569, a previously known threat actor and once the main player in “fake update” campaigns. TA2727, on the other hand, according to Proofpoint’s blog post, is actively distributing malware itself, often employing the “fake update” ruse to trick users.
One recent campaign observed TA2727 delivering different malware based on the victim’s location. In the United States and Canada, users were directed to the SocGholish inject, which led to the installation of malware. But in Europe, Windows users encountered a fake browser update prompt that installed the Lumma Stealer, while Android users were targeted with the Marcher banking trojan.
FrigidStealer macOS Malware
The new FrigidStealer targets Mac users, and the attack starts with a fake update message that redirects them to a malicious file. If clicked, the file, disguised as a browser update (both Chrome and Safari), installs the information stealer. FrigidStealer then secretly harvests sensitive data like browser cookies, files related to passwords and cryptocurrencies, and even Apple Notes, just like the recently spotted new variant of the XCSSET malware.
The malware is written in Go and uses WailsIO, a framework that allows the fake update window to look realistic. It also bypasses Mac’s Gatekeeper security feature by requiring users to right-click and select “Open,” a common trick used by Mac malware authors.
Windows and Android Users Also Targeted
Mac users aren’t the only ones at risk. The same attack chain has been found delivering Marcher banking trojan for Android and Lumma Stealer and DeerStealer for Windows.
For Android users, clicking the update downloads Marcher, a banking trojan that has been active since 2013 and is designed to steal login credentials from banking apps. If a Windows user clicks the fake update, they receive an MSI installer that loads a trojanized DLL, ultimately running Lumma Stealer to extract credentials and financial data.
Users can still protect themselves by learning basic cybersecurity practices, learning how to spot a phishing email, avoiding third-party apps and tools, and scanning files and links on sites like VirusTotal or ANY.RUN.