What started as a single suspicious browser add-on has grown into a much larger cybersecurity concern that many users never saw coming. Last month, Koi Security published an analysis of a Firefox extension it named GhostPoster, describing a method of abuse that avoided the usual warning signs reviewers look for when scanning browser extensions.
GhostPoster’s modus operandi included hiding the payload inside a harmless looking PNG image file. That image was later decoded and executed, allowing the extension to bypass static analysis tools and manual reviews without raising suspicion.
LayerX After Koi Security
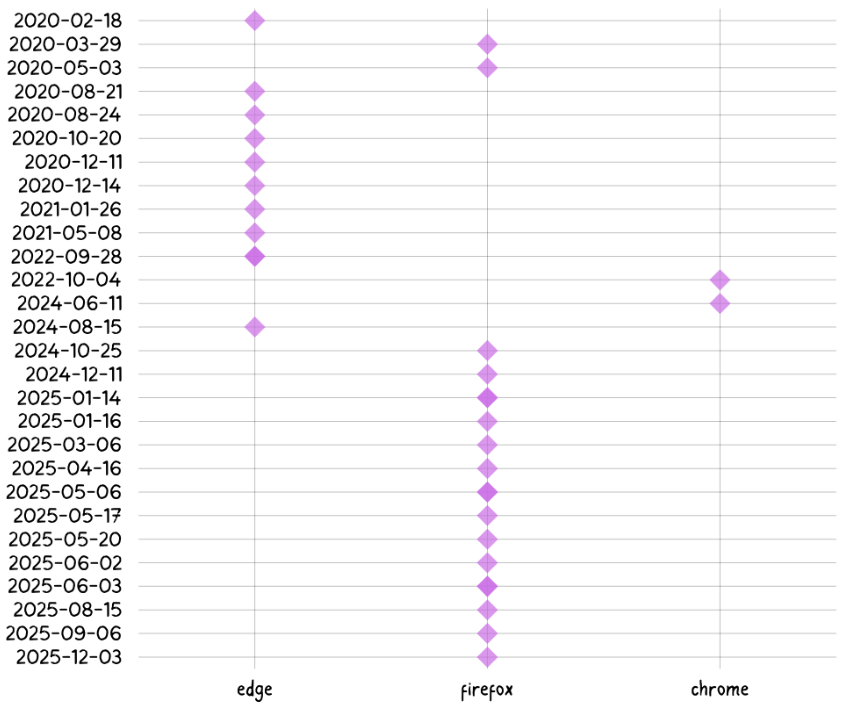
After Koi shared its findings, LayerX began tracing the infrastructure behind the extension. Their investigation revealed 17 more add-ons using the same backend systems and operating playbook. Combined, those extensions were installed more than 840,000 times, with some sitting on user devices for nearly five years without detection.
LayerX also noted the presence of a more advanced variant within the same campaign that relied on additional evasion methods and accounted for 3,822 installs on its own. While smaller in number, the design showed careful planning and patience rather than quick profit.
“Following their publication, our investigation identified 17 additional extensions associated with the same infrastructure and tactics, techniques, and procedures (TTPs). Collectively, these extensions were downloaded over 840,000 times, with some remaining active in the wild for up to five years.”
LayerX
The campaign itself did not begin on Firefox. Investigators traced its early activity to Microsoft Edge, where it later spread to Chrome and Firefox as the infrastructure matured. Researchers believe that the slow expansion suggests a long-term operation that favored persistence over speed, letting extensions remain useful and trusted before activating harmful behavior.
Extensions Removed From Marketplaces, Not From Browsers
In response to the disclosures, as per layerX’s blog post shared with Hackread.com, Mozilla and Microsoft removed the identified extensions from their official stores. The removals stop new downloads, but extensions already installed continue running on user systems, which means users must remove them manually.
The findings go on to show how extensions have become easiast way for cyber criminals to compromise browser security. Therefore, users must regularly review installed extensions, limit permissions, and remove anything that is no longer needed.