According to Google’s Project Zero team, threat actors exploited 0-day vulnerabilities to successfully carry out their attack.
The IT security researchers at Google’s Project Zero have disclosed details of a complex hacking campaign that they discovered around one year back in early 2020.
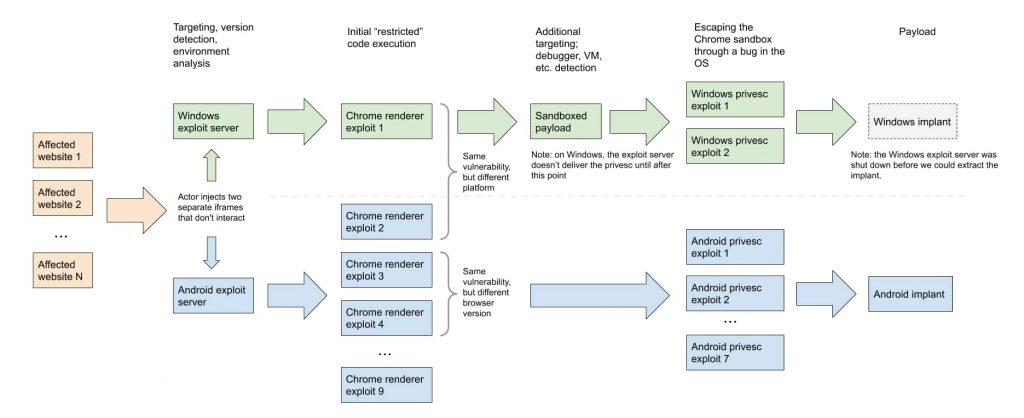
In an in-depth, six-part analysis of the campaign that targeted Windows and Android users, researchers have explained how threat actors managed to carry out a watering hole attack using 0-day and n-day exploits.
See: Google reveals unpatched 0day vulnerability in Microsoft’s API
Project Zero researchers collaborated with Google Threat Analysis Group to probe the watering hole attack and the two exploits, each of which utilized a separate exploit chain to compromise the target(s).
A ‘Sophisticated Actor’ Developed Exploit Chains
Project Zero states that the campaign is most definitely the work of a ‘highly sophisticated actor,’ operating a complex targeting infrastructure. However, they didn’t indicate who that actor may be. They did note that the discovered exploit chains were designed for flexibility and efficiency through modularity.
According to researchers, they were ‘well-engineered, complex code with a variety of novel exploitation methods, mature logging, sophisticated and calculated post-exploitation techniques, and high volumes of anti-analysis and targeting checks,” the report reads.
“We believe that teams of experts have designed and developed these exploit chains,” researchers noted.
Exploits for Four Bugs Found in Google Chrome
The research team discovered exploits for four bugs in the Google Chrome web browser. One of the bugs was a 0-day, and two 0-days exploited font rendering vulnerabilities in MS Windows.
They also noticed that a heap buffer overflow bug was present in the Client/Server Runtime Subsystem (CSRSS). This bug was abused to evade sandboxing or the operating system’s software execution restrictions. For Android devices, the threat actors used known exploits.
Hence, the attack had four stages. The attackers used a Google 0-day vulnerability in stage 1. In stage 2, they utilized a public exploit for Android n-days. A comprehensively designed and engineered, mature, and complex exploit was reserved for stage 3.
See: Will Microsoft add Android support to Windows 10 next year?
Additionally, they would download the final payload in stage 3 as well, which led researchers to believe that the threat actors most likely had more ‘device-specific 0-day exploits.’
- CVE-2020-6418 – Chrome Vulnerability in TurboFan (fixed February 2020)
- CVE-2020-0938 – Font Vulnerability on Windows (fixed April 2020)
- CVE-2020-1020 – Font Vulnerability on Windows (fixed April 2020)
- CVE-2020-1027 – Windows CSRSS Vulnerability (fixed April 2020)
A trove of Valuable Information Collected
Project Zero researchers collected valuable information from the two exploit servers, including rendered exploits for the four Chrome bugs, two sandbox escape exploits that abused three N-day vulnerabilities in Windows-based systems, and a privilege escalation kit containing known n-day exploits for older Android versions.
The attackers used Chrome exploits to execute malicious code on their targeted devices remotely. They used n-days for Android and 0-days for Windows devices. They had shut down the Windows attack server before Google’s researchers could extract the implant.
Did you enjoy reading this article? Don’t forget to like our page on Facebook and follow us on Twitter!










Everything is a hack or an ad jack or browser high jack.
Maybe if everything wasnt an open door for law enforcement to exploit or their big data companies to proliferate the world could avoid these problems.
Or is it all just exactly that? Problems