Hacker IntelBroker claims to have breached Hewlett Packard Enterprise (HPE), exposing sensitive data like source code, certificates, and PII, now available for sale online.
The notorious IntelBroker hacker along with their associates have claimed responsibility for breaching Hewlett Packard Enterprise (HPE), a Houston, TX, United States-based global company that provides technology solutions to businesses.
The hacker, who was previously linked to several high-profile data breaches, is now selling the allegedly stolen data, demanding payment in Monero (XML) cryptocurrency to remain anonymous and untraceable.
This was revealed to Hackread.com by the hacker himself and later announced on Breach Forums, a cybercrime and data breach forum administered by the hacker. In an exclusive conversation with Hackread.com, IntelBroker claimed that the breach was the result of a direct attack on HPE’s infrastructure and did not involve compromising a third party for access, as has been common in recent attacks.
What’s in the Allegedly Stolen Data?
IntelBroker also shared a data tree and two screenshots allegedly taken from the company’s internal infrastructure. The data tree, analyzed by Hackread.com, appears to reference a development or system environment involving both open-source software and proprietary package management systems.
Additionally, the hacker claims to have extracted sensitive data, including source code, private GitHub repositories, Docker builds, certificates (both private and public keys), product source code belonging to Zerto and iLO, user data such as old PII related to deliveries, and access to APIs, WePay, self-hosted GitHub repositories, and more.
During Hackread.com’s initial analysis of the alleged data tree, several findings align with the hacker’s claims. The directory structure includes private keys and certificates, such as ca-signed.key and hpe_trusted_certificates.pem, suggesting possible exposure to sensitive cryptographic material.
Source code for HPE products like iLO and Zerto is present, with files such as ilo_client.py and zerto_bootstrapper.py hinting at leaked proprietary implementations. References to .github directories and .tar archives for private repositories further point to compromised development assets.
Additionally, the presence of files like VMW-esx-7.0.0-hpe-zertoreplication.zip and ZertoRunner.exe suggests the possible leak of compiled software packages and deployment files. If verified by HP, this could be a major security incident.
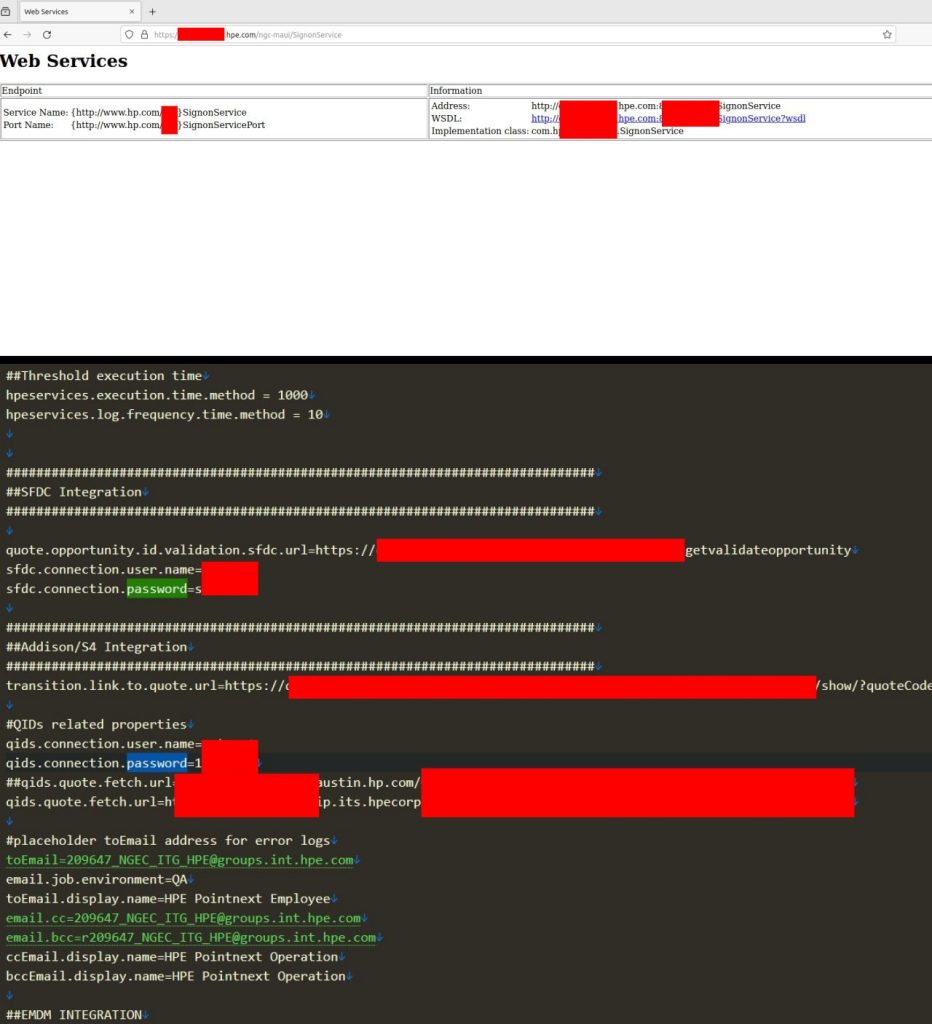
The following image combines two screenshots shared by the hacker, providing detailed insights into Hewlett Packard Enterprise’s internal systems. The first screenshot shared by the hacker shows details of Hewlett Packard Enterprise’s internal SignonService web service. The image displays the service’s endpoint address, WSDL link, and implementation class, potentially exposing sensitive infrastructure information.
The second screenshot reveals sensitive configuration details from Hewlett Packard Enterprise’s internal systems. The image exposes credentials for Salesforce and QIDs integrations, internal URLs for SAP S/4 HANA quoting services, and placeholder email addresses for error logging, potentially highlighting serious security vulnerabilities within HPE’s infrastructure.”
HPE and HP, What’s the Difference?
While the names Hewlett-Packard Enterprise (HPE) and HP Inc. are often used interchangeably, they are two different companies with different focuses. In 2015, Hewlett-Packard split into two separate entities. HP Inc. continues to specialize in consumer products like laptops, desktops, and printers, while Hewlett-Packard Enterprise (HPE) focuses on providing enterprise-level IT solutions, including servers, storage, networking, and cloud computing.
Both companies are separate with independent ownership and management. The mention of this distinction is important, as the reported breach specifically targets HPE, not HP Inc.
HPE and Cybersecurity Incident – Not a One-Time Thing
This isn’t HPE’s first brush with a cybersecurity incident. In January 2024, the company disclosed to the SEC that Russian state-sponsored hackers associated with Midnight Blizzard (also known as Cozy Bear) had breached its servers. The attack, which began in May 2023, targeted a small percentage of HPE mailboxes belonging to employees in cybersecurity, go-to-market, business segments, and other critical functions, resulting in data theft.
In 2018 hackers affiliated with China’s Ministry of State Security reportedly infiltrated Hewlett Packard Enterprise’s networks. These attacks were part of a broader Chinese cyber campaign known as Cloudhopper.
Right After the CICSO Incident
Intel Broker is known for high-profile data breaches. In October 2024, the hacker announced breaching Cisco and stealing terabytes of data. Cisco later confirmed that the stolen data originated from a misconfigured, public-facing DevHub resource that was exposed without password protection, allowing hackers to download it.
In November 2024, the hackers claimed to have breached Nokia through a third-party contractor. The data was being sold for $20,000. The same hackers boasted about breaching AMD (Advanced Micro Devices, Inc.), and stealing employee and product information.
UPDATE: Following Hackread.com’s viral report on the alleged breach, HPE has confirmed it is investigating the hackers’ claims.