Cybersecurity researchers at Forcepoint X-Labs have spotted a new and tricky malware campaign that has been spreading and infecting targeted devices with VenomRAT, a remote access trojan known for targeting researchers in fake PoC (Proof of Concept) attacks
In this campaign, instead of the usually infected documents or executable files, cybercriminals are delivering the dangerous VenomRAT hidden inside a virtual hard disk image file (.vhd).
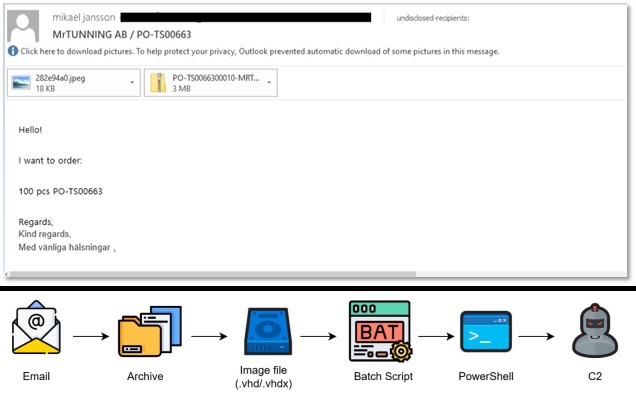
The campaign begins with a phishing email. This time, the bait is an apparently harmless purchase order. However, opening the attached archive doesn’t reveal a typical document. Instead, users find a .vhd file – a container that mimics a physical hard drive.
When a user opens the .vhd file, their computer treats it like a new drive. But this isn’t a drive full of legitimate files; it contains a malicious batch script designed to cause harm. Using a .vhd file to spread malware is a new trick. Since these files are commonly used for disk imaging and virtualization, security software doesn’t always flag them as a threat.
“This is a unique approach,” explains Prashant Kumar, a Security Researcher at Forcepoint X-Labs. “Attackers are constantly looking for ways to evade detection, and hiding malware within a virtual hard disk image is a good example of that.”
The Attack and Stealing User Data
According to research from Forcepoint X-Labs, shared with Hackread.com, the malware script is disguised with multiple layers of code and executes a series of malicious activities once activated. It starts by self-replicating, making sure a copy remains available at all times.
Then, it launches PowerShell, a legitimate Windows tool often exploited by attackers, and establishes persistence by placing a malicious script in the Startup folder, allowing it to run automatically whenever the user logs in. To dig in even more, the script modifies Windows registry settings, making it harder to detect and remove.
The malware also employs hidden communication by connecting to Pastebin, a popular text-sharing platform, to fetch instructions from a remote command-and-control (C2) server, which serves as the attacker’s command hub. Once established, the malware initiates data theft, logging keystrokes and storing sensitive information in a configuration file. It also downloads additional components, including a .NET executable, to assist in encryption and system manipulation.
Researchers noted that this VenomRAT variant uses HVNC (Hidden Virtual Network Computing), a remote control service that allows attackers to control the infected system without detection.
What’s Next for Unsuspected Users?
Be careful with email attachments, even if they seem legitimate; especially if they come from unknown senders. If you receive an unexpected invoice or purchase order, don’t trust the contact details in the email; verify it directly with the sender using a known phone number or email.
Keeping your operating system, antivirus, and security tools up to date is critical for blocking threats from executing on your system. Lastly, make sure your team knows how to spot and report phishing attempts. Awareness and common sense are two of the best cybersecurity measures anyone can use, anywhere and at all times.