Researchers believe that the new Jupyter infostealer is being operated by Russian speaking hackers.
For malicious hackers, there are different types of trojans out of which one happens to be an infostealer. These are built for stealing data from systems and communicating it to their servers without having long-term objectives such as remaining hidden within the system.
Keeping this in mind, recently, researchers from Morphisec have discovered a new info stealer written in .NET called Jupyter which targets notable web browsers such as Mozilla Firefox and Google Chrome in addition to the Chromium code in itself.
According to researchers,
This is the first version seen in the wild of the infostealer stealing information (autocomplete, cookies, and passwords) only from Chrome browsers.
This version added Firefox information stealing (cookies, logins, certificates, and form history). This version uses the same technique of copying the stolen information before accessing it to evade detection.
Stumbling across it while helping one of their customers in the US, the features of the malware include the ability to download and run malware plus Powershell scripts and commands while also injecting shellcode into different applications that relate to Windows Configuration.
See: Fake Chrome & Firefox browser update lead users to malware infection
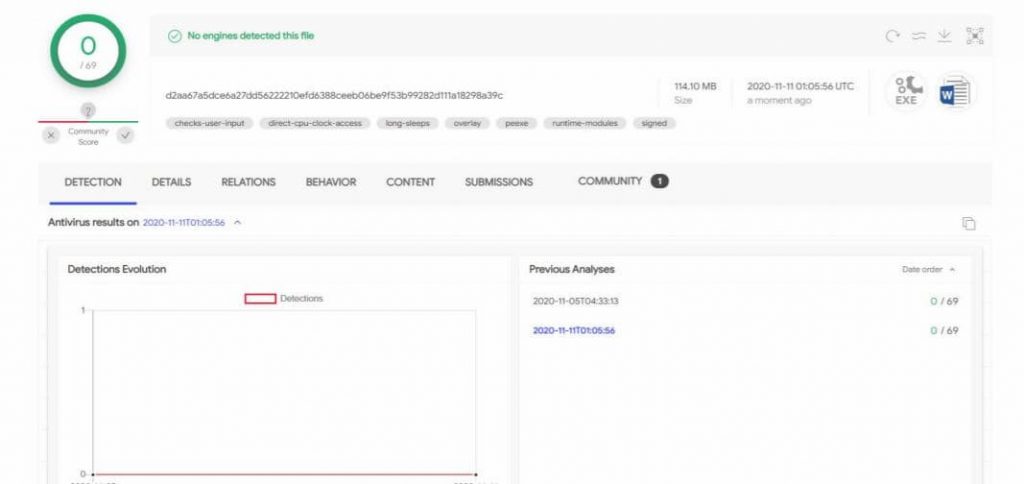
The downloaded file that is run appears to be a Zip file with an installer that shows itself as another legitimate piece of software while in actuality is not. The alarming thing here is that this file according to the researchers has maintained a 0% detection rate in VirusTotal for over 6 months making us wonder how many systems it may have had infected by now.
Explaining further, the researchers stated in their blog post that,
Upon execution of the installer, a .NET C2 client (Jupyter Loader) is injected into a memory. This client has a well defined communication protocol, versioning matrix, and has recently included persistence modules.
The client then downloads the next stage, a PowerShell command that executes the in-memory Jupyter.NET module.
Currently, all clues about the source origin of the malware point to Russia based on the different Command & Control Servers identified despite a lot of them now being inactive.
See: Hackers found tracking web traffic of Chrome and Firefox browsers
Secondly, the researchers reverse searched an image of the C2 server admin panel and found the exact same match on Russian forums. If that was not enough, the name of the malware itself, Jupyter comes across as a “Russian to English misspelling of the planet name”.
To conclude, this trend is nothing new in itself because researchers have constantly observed new variants of existing malware types being developed and even going unnoticed. Such research reports are a relief in the face of such calamities helping the cybersecurity community mend their blind spots.
Did you enjoy reading this article? Do like our page on Facebook and follow us on Twitter.