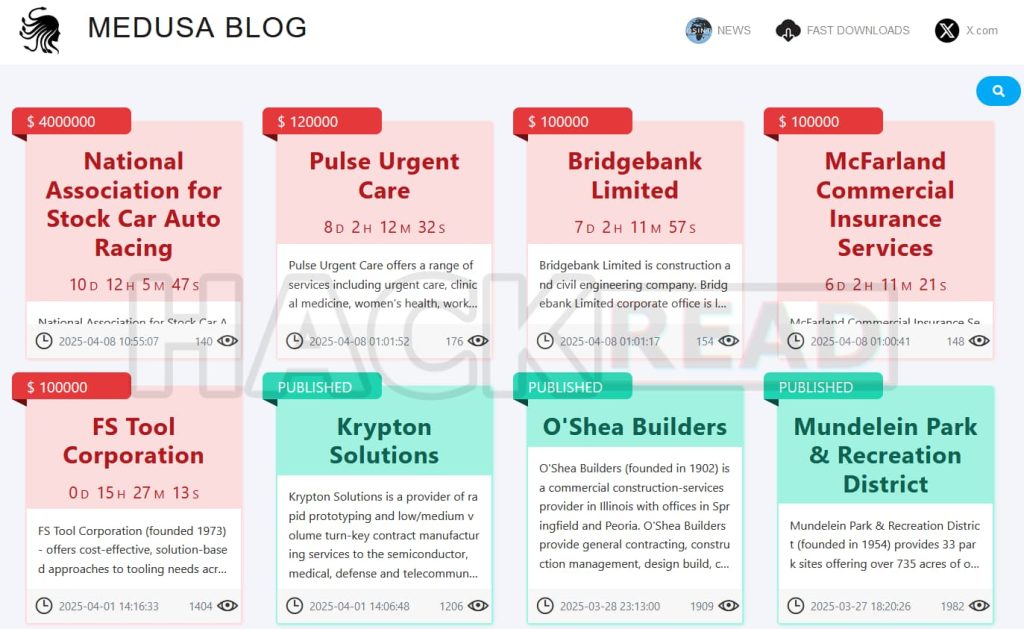
The Medusa ransomware gang has added another high-profile name to its growing list of victims. Earlier today, the group listed NASCAR (National Association for Stock Car Auto Racing) on its dark web leak site, demanding a $4 million ransom and threatening to release internal data if payment isn’t made. Alongside NASCAR, the group is also claiming McFarland Commercial Insurance Services, Bridgebank Ltd, and Pulse Urgent Care as new victims.
As seen by Hackread.com, the hackers have already posted 37 document images related to NASCAR as proof. A review of one of the blurred images shows a mix of corporate branding materials, facility maps, spreadsheets with employee contact details, and what looks like internal notes and photographs.
A quick analysis of the leaked documents suggests some of the content includes detailed maps of raceway grounds, email addresses, names and titles of staff, and credential-related info, which suggests a real compromise of operational and logistical data.

FBI Warned U.S. Organizations About Medusa in March 2025
The Medusa ransomware group was first spotted in the wild back in 2021, but its activity has picked up speed over the past couple of years. One of its better-known attacks was against the Minneapolis Public Schools district in 2023, where the group leaked sensitive student and employee data after a $1 million ransom demand went unmet. They’ve also targeted hospitals, telecom firms, and municipalities, often dumping large amounts of internal files when ransoms aren’t paid.
Medusa also made the news just a couple of weeks ago for using stolen digital certificates to disable anti-malware tools on infected systems. That tactic, which was flagged in a March 25 report, allowed them to operate within networks and avoid detection.
On March 13 2025, the FBI and Cybersecurity and Infrastructure Security Agency (CISA) issued a joint advisory urging organizations to strengthen their security measures. The advisory specifically recommended enabling two-factor authentication and monitoring systems for signs of unauthorized certificate use, clearly concerned about the direction Medusa’s attacks were heading.
NASCAR has Yet to Respond, Acknowledge, or Deny
It’s important to note that this coverage is based solely on claims made by the Medusa ransomware group. NASCAR has yet to respond, acknowledge, or deny these claims.
However, if the organization does confirm the breach, it wouldn’t be surprising; NASCAR generates hundreds of millions in revenue each year, making it an attractive target for cybercriminals.
This also isn’t the first time NASCAR has been linked to a ransomware incident. In July 2016, a prominent NASCAR team suffered a major ransomware attack when its chief’s computer was infected with a TeslaCrypt variant. The attackers encrypted all files on the system and demanded payment in Bitcoin.