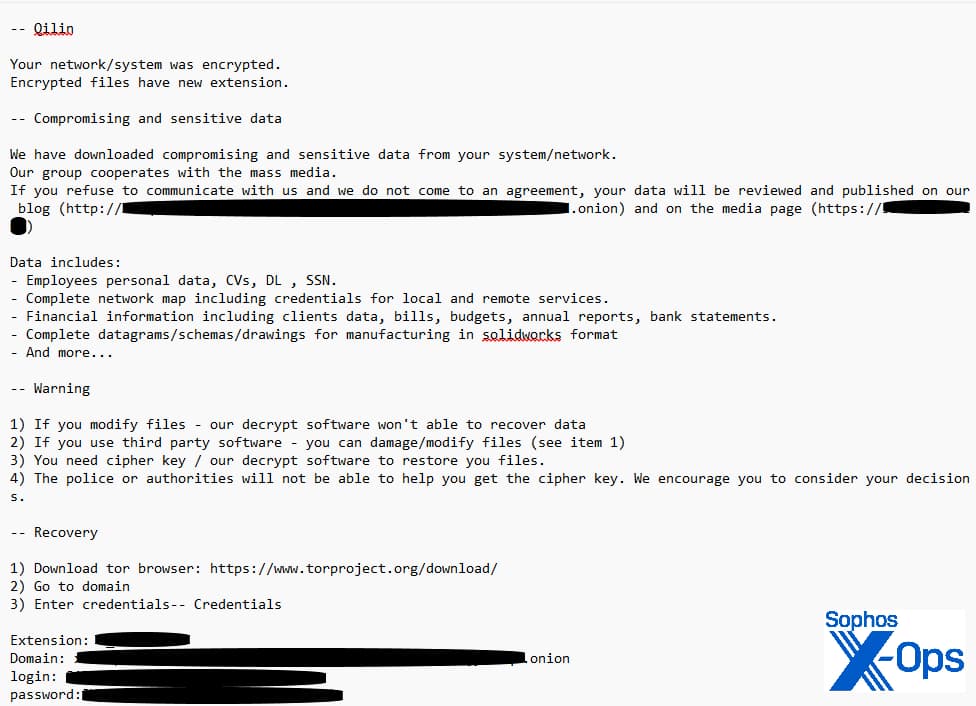
Qilin ransomware is evolving, now targeting Google Chrome credentials. Learn how this new tactic expands their attack arsenal and how organizations can protect themselves. Discover mitigation strategies and the importance of robust security measures.
Cybersecurity researchers at Sophos have uncovered a concerning development in the Qilin ransomware operation: Credential harvesting through Google Chrome browsers.
According to the company, while investigating the Synovis breach Sophos X-Ops team identified that the attackers stole credentials stored in Google Chrome browsers on a subset of the network’s endpoints.
For your information, on June 3, 2024, the Qilin ransomware gang targeted Synnovis, an outsourced lab service provider for NHS hospitals in South-East London, claiming to have stolen hospital and patient data and demanding $50 million in ransom. After failed negotiations, the gang publicly leaked their entire exfiltrated dataset.
Qilin attacks have historically involved “double extortion,” stealing data, encrypting systems, and threatening to reveal/sell it if the victim doesn’t pay the ransom, which Sophos calls Turning the Screws technique.
However, this discovery marks a significant shift in Qilin’s tactics as it targeted credentials stored on infected networks’ Google Chrome, a browser that occupies around 65% of the browser market. This may have far-reaching consequences as attackers can access financial accounts, email, cloud storage, or business applications using compromised credentials.
The Sophos IR team observed this activity in July 2024 on a single domain controller within the target’s Active Directory domain. Other domain controllers in that domain were affected differently by Qilin, highlighting the potential for similar attacks in the future.
Researchers analyzed a Qilin attack that began with compromised VPN credentials, suggesting the initial access may have been purchased from an Initial Access Broker (IAB). This 18-day dormancy period indicates a calculated approach, allowing the attackers to map the network, identify critical assets, and plan their next move.
The credential theft itself leverages a custom stealer designed to target Google Chrome. Once the ransomware gains a foothold, it deploys Group Policy Objects (GPO) to automate the process across the network. This automation significantly increases the efficiency of the attack and ensures a wider reach within the compromised environment.
“A successful compromise of this sort would mean that not only must defenders change all Active Directory passwords; they should also (in theory) request that end users change their passwords for dozens, potentially hundreds, of third-party sites for which the users have saved their username-password combinations in the Chrome browser. The defenders of course would have no way of making users do that,” Sophos’ researchers explained in a blog post.
First appearing in October 2022, Qilin has quickly gained notoriety for its RaaS (Ransomware-as-a-Service) model, offering its malicious tools to other cybercriminals. It’s believed to be linked to Russia-based threat actors and has targeted various industries, including street newspapers, automotive parts giants, and even Australian court services.
The evolving tactics of Qilin ransomware highlight the importance of continuous threat monitoring and adaptation of security strategies. Organizations must implement MFA (multi-factor authentication) on remote access solutions to enhance security, use robust endpoint security solutions to detect and prevent suspicious behaviour, and regularly backup data and patch all network systems, including operating systems and web browsers.