SUMMARY
- Rockstar 2FA Exposed: Trustwave uncovers Rockstar 2FA, a phishing-as-a-service (PhaaS) platform targeting Microsoft 365 accounts with advanced tools.
- 2FA Bypass: Features include 2FA cookie harvesting, antibot protections, and fake login pages mimicking legitimate services.
- Credential Theft: Attackers capture login credentials and session cookies through adversary-in-the-middle (AiTM) tactics.
- Wide Impact: Linked to over 5,000 phishing domains and large-scale attacks across multiple industries since May 2024.
- Accessible for Hackers: Affordable subscriptions make phishing accessible to attackers with minimal technical skills.
Cybersecurity researchers at Trustwave have discovered “Rockstar 2FA,” a phishing-as-a-service platform designed to help hackers and script kiddies bypass two-factor authentication (2FA) and gain unauthorized access to Microsoft 365 accounts.
This platform has already been linked to a surge in large-scale adversary-in-the-middle (AiTM) attacks targeting users across multiple sectors and regions, which have been successful in stealing Microsoft 365 credentials from unsuspecting victims.
How Rockstar 2FA Works?
Rockstar 2FA is an upgraded version of the DadSec/Phoenix phishing kit, which was behind some of the most global phishing campaigns in 2023, including attacks on major U.S. school districts in December 2023.
The platform’s features include 2FA bypass, 2FA cookie harvesting, antibot protection, login page themes mimicking popular services, fully undetectable (FUD) links, and Telegram bot integration.
Rockstar 2FA also provides a user-friendly admin panel that allows customers to track the status of their phishing campaigns, generate URLs and attachments, and personalized themes. The platform is offered as a subscription service, with prices starting at $200 for a two-week subscription.
The Phishing Campaign
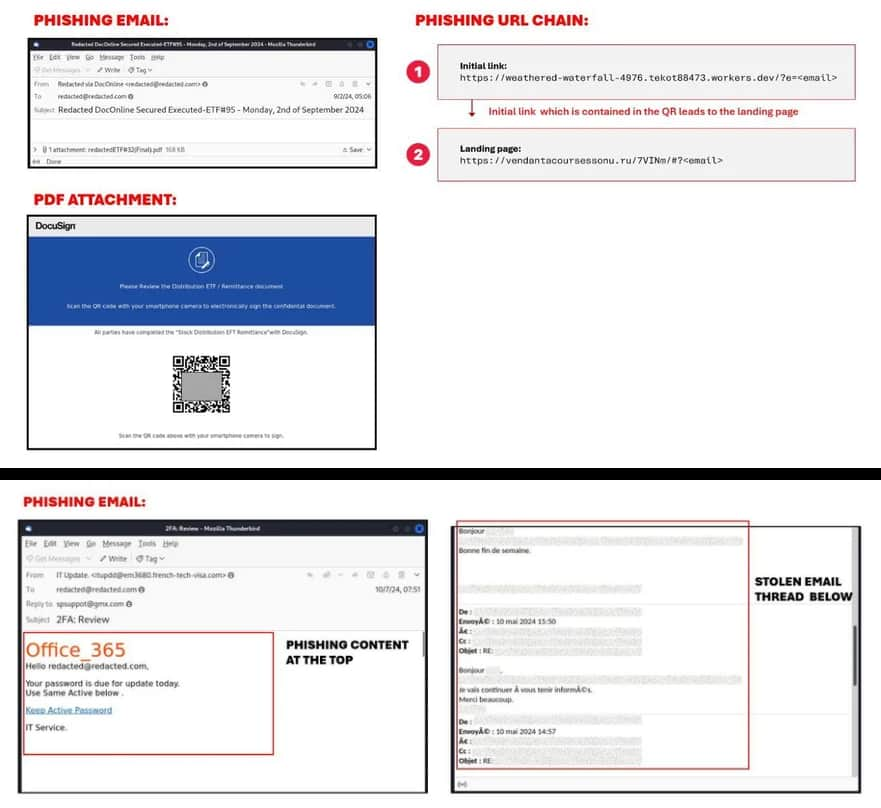
The phishing campaign associated with Rockstar 2FA uses various email delivery mechanisms, including compromised accounts and abused legitimate services such as email marketing platforms. The emails are designed to trick victims into entering their credentials on a fake login page that mimics Microsoft 365.
Most importantly, once a victim clicks on a malicious link, they are redirected to a landing page that presents a Cloudflare Turnstile challenge. This challenge is designed to prevent automated analysis of the phishing page and only allows legitimate users to proceed. If the user passes the challenge, they are presented with a phishing page that closely resembles the sign-in page of the brand being imitated.
Once the victim enters their credentials, the AiTM server then acts as a proxy, forwarding the credentials to Microsoft’s legitimate service to complete the authentication process. Once the authentication is complete, the server captures the session cookie, which can be used by the attackers to gain direct access to the victim’s account, even if it’s protected by MFA.
The Impact
According to Trustwave’s blog post shared with Hackread.com ahead of publishing on Monday, the Rockstar 2FA platform has led to large-scale phishing attacks using sophisticated tactics, techniques, and procedures (TTPs).
The platform’s ability to bypass 2FA protections has increased the possibility of secondary attacks, such as account takeovers, launching phishing campaigns using compromised accounts, or performing business email compromise (BEC) attacks.
What’s more, the Rockstar 2FA platform has been linked to over 5,000 hits on urlscan.io since May 2024, with a noteworthy increase in activity in August 2024.
“One distinguishable characteristic of this campaign is the incorporation of car-themed web pages. Via urlscan.io, we were able to find over 5,000 hits of car-themed domains linked to this campaign since May 2024.”
Trustwave
According to Krishna Vishnubhotla, Vice President of Product Strategy at Zimperium, “PhaaS platforms like Rockstar 2FA are lowering the cost of entry for new attackers, mainly through mobile devices. By providing ready-made phishing kits, these platforms eliminate the need for extensive technical skills or resources usually required for phishing attacks.”
The growing use of Rockstar 2FA highlights how phishing has become a highly lucrative tactic for cybercriminals. To stay safe, avoid clicking links or downloading attachments from unknown emails, double-check before entering your credentials on a login page, and scan links and files using tools like VirusTotal.
For employees, simulated phishing training is far more effective than basic cybersecurity training in helping them recognize and respond to phishing threats.