Despite tighter security from Apple and Google, hackers and cybercriminals continue to exploit rooted and jailbroken devices for their attacks. A new report from mobile security firm Zimperium shared with Hackread.com ahead of its publishing on Thursday, warns that compromised mobile phones remain a major risk for businesses, as these devices are far more likely to be targeted by malware and system takeovers.
What Are Rooting and Jailbreaking?
Rooting (on Android) and jailbreaking (on iOS) give users full control over their devices. This allows customization beyond what manufacturers allow and also removes key security protections. A rooted or jailbroken can’t enforce security protocols like Google’s Play Integrity or Apple’s security checks, but they can install apps from unverified sources, disable security features, and modify system files, making them prime targets for cybercriminals.
According to Zimperium’s research, rooted Android devices are:
- 3.5 times more likely to be attacked by malware
- 250 times more likely to suffer a system compromise
- 3,000 times more likely to experience a filesystem breach
Depending on who the targeted victim is, a compromised phone can be used as an entry point into corporate networks, allowing attackers to steal sensitive data, launch phishing campaigns, and bypass OTPs.
A Well-Equipped Toolkit of Hackers
The security industry has worked hard to detect and block rooted devices, but hackers have also been catching up. Tools like Magisk, APatch, KernelSU, Dopamine, and Checkra1n are in active development, with some even designed to hide their presence to avoid scans.
Magisk, for example, uses a “systemless” root method that avoids modifying core system files, making them harder to detect. APatch takes a different approach by modifying kernel memory on the fly, leaving no permanent traces. These updated toolkits make it increasingly difficult for cybersecurity researchers to spot compromised devices before damage is done.
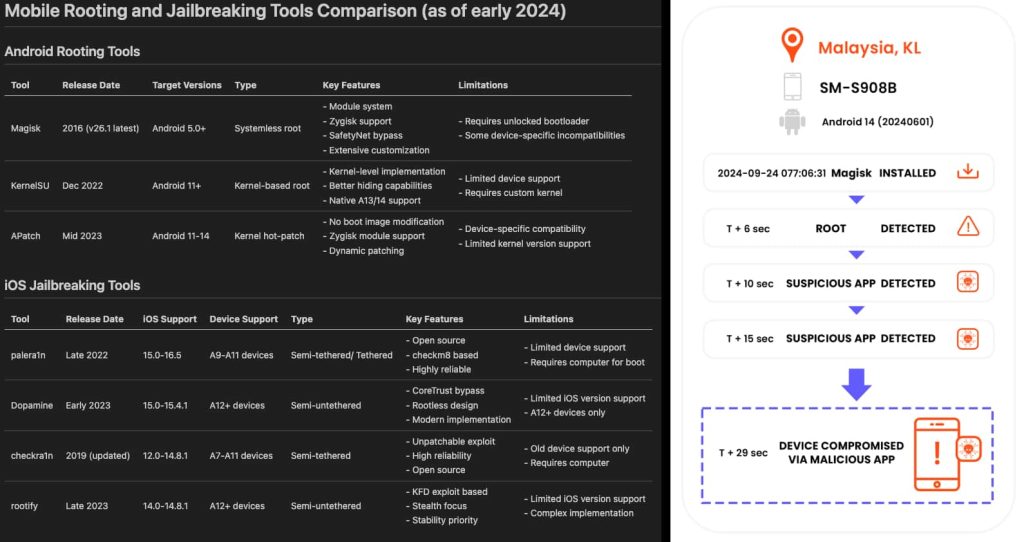
Decline in Rooting and Jailbreaking but Still a Threat
Rooting and jailbreaking were a big deal from 2011 to 2019. Now that the number of rooted and jailbroken devices has declined, they still pose a serious risk, especially in workplaces where employees use personal phones for work.
Worse, this threat is not limited to small businesses; even employees at cybersecurity giants like Kaspersky Labs have had their iPhones infected by malware. A single compromised phone can give attackers access to corporate data, email accounts, and internal applications.
J. Stephen Kowski, Field CTO at cybersecurity firm SlashNext, highlights the issue, “When employees root or jailbreak their devices, they’re removing crucial security guardrails. This creates significant attack vectors for threat actors. Businesses need advanced threat detection that can identify compromised devices and block attacks without disrupting workflows.”
Nevertheless, companies need to take mobile security seriously. Traditional security solutions often fail to detect modern rooting tools, so businesses should invest in advanced mobile threat detection that can identify cybersecurity threats in real time. Here’s how a company can start tackling this threat:
- Educating employees on the risks of rooting and jailbreaking
- Using mobile security solutions that detect hidden modifications
- Blocking rooted and jailbroken devices from accessing corporate networks
- Implementing strict app policies to prevent sideloading of unverified software.









