Cofense uncovers new LinkedIn phishing scam delivering ConnectWise RAT. Learn how attackers bypass security with fake InMail emails and how to protect against this sophisticated phishing tactic.
Cybersecurity researchers at Cofense have recently uncovered a deceptive campaign that distributes malicious software using a spoofed LinkedIn email. This operation, detected by their Phishing Defense Center and Intelligence teams, diverges from typical LinkedIn-themed phishing attacks, which usually aim to steal user credentials or facilitate business email compromise. Instead, this campaign delivers a remote access trojan called ConnectWise RAT.
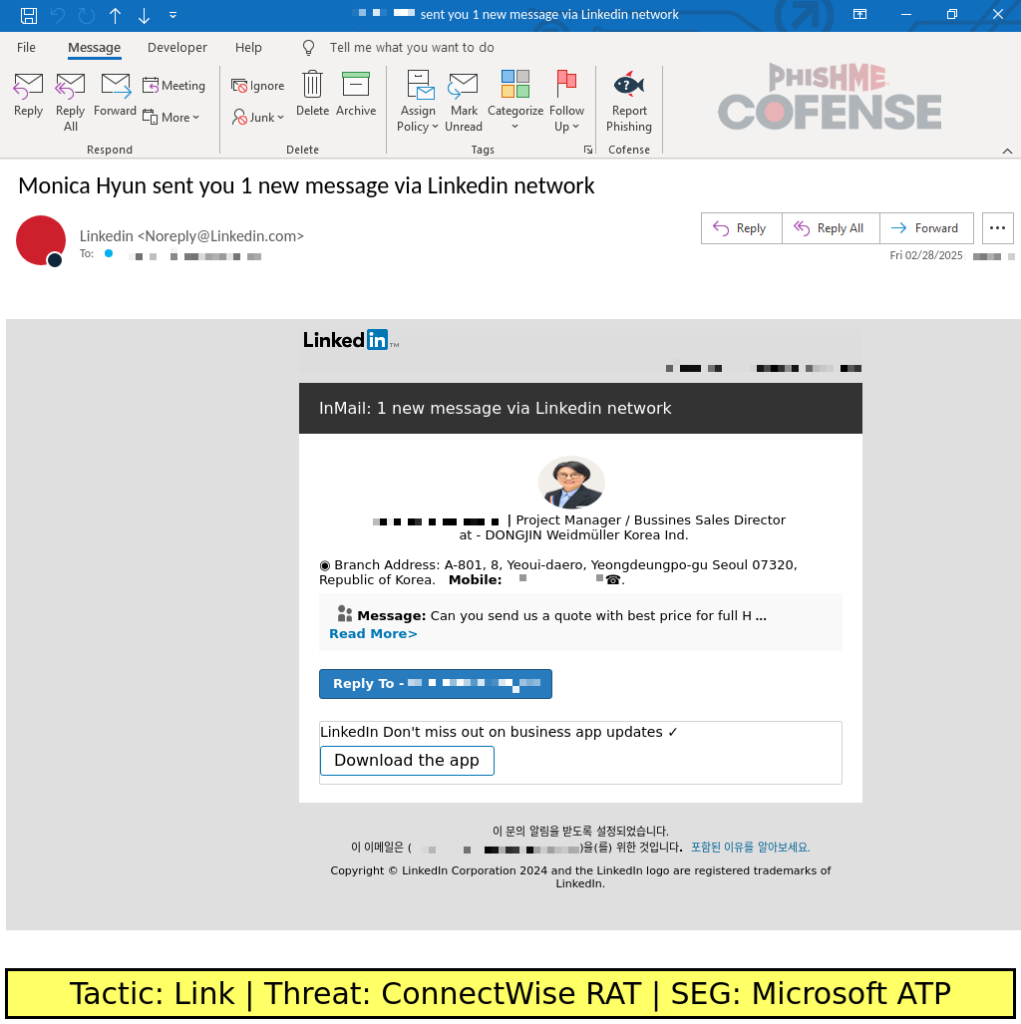
The fraudulent email is designed to mimic a notification for a LinkedIn InMail message, a feature that allows users to contact individuals outside of their immediate network. The email effectively leverages LinkedIn’s branding, convincingly creating legitimacy. However, careful examination reveals that the email uses an outdated template, reminiscent of LinkedIn’s design prior to its 2020 user interface and branding overhaul.
The email’s narrative centres around a supposed sales director from a company requesting a product or service quote. This strategy aims to create a sense of urgency, prompting the recipient to respond quickly. However, the sender’s identity and the company mentioned are fabricated.
The profile picture used in the email belongs to a real individual, Cho So-young, who is the president of a Korean civil engineering organization, whereas the company name (DONGJIN Weidmüller Korea Ind) combines elements of two legitimate corporations, but this company does not exist.
Clicking the “Read More” or “Reply To” buttons embedded within the email triggers the download of the ConnectWise RAT installer. Interestingly, the email avoids the common tactic of directly prompting users to download or run a file. This subtle approach might be designed to bypass the suspicions of users who are trained to be wary of such direct requests.
Analysis of the email’s security headers reveals that it fails Sender Policy Framework (SPF) and DomainKeys Identified Mail (DKIM) authentication checks, indicating that the email was not sent from a legitimate LinkedIn server and was not digitally signed.
Despite these red flags, the email bypassed existing security measures, likely due to the Domain-based Message Authentication, Reporting & Conformance (DMARC) policy being configured to mark the email as spam rather than outright rejecting it.
This campaign has been active since at least May 2024, with the email template remaining consistent. However, whether earlier iterations of this campaign also delivered the ConnectWise RAT remains unconfirmed.
“This campaign was found to exist in the wild as far back as May 2024. While the email template has not changed since then, Cofense Intelligence was unable to confirm whether this campaign was used to deliver ConnectWise RAT in prior samples that were found via open-source intelligence,” researchers noted in the blog post.
Nevertheless, this campaign highlights the evolving tactics of cybercriminals and the persistent threat of sophisticated phishing attacks involving LinkedIn. Protection against such threats requires educating employees to carefully scrutinize email senders especially those requesting urgent actions, appropriately configuring email authentication protocols (SPF, DKIM, and DMARC), and ensuring your Secure Email Gateway (SEG) is configured to effectively filter and block suspicious emails.