Massive Twitter (X) profile data leak exposes details of 2.8 billion users; alleged insider leak surfaces with no official response from the company.
A data leak involving a whopping 2.87 billion Twitter (X) users has surfaced on the infamous Breach Forums. According to a post by a user named ThinkingOne, the leak is the result of a disgruntled X employee who allegedly stole the data during a period of mass layoffs. If true, this would be the largest social media data leak in history, but surprisingly, neither X nor the broader public appears to be aware of it.
What We Know About the Leak
The original post by ThinkingOne states that the data, around 400GB worth, was likely exfiltrated during messy layoffs at X. The poster claims that they tried contacting X through multiple methods but received no response.
Frustrated with the lack of acknowledgment from X and the general public, they took matters into their own hands and decided to merge the newly leaked data with another infamous breach from January 2023.
The 2023 Breach Recap
To understand the full scope of what was leaked, looking at the 2023 X data breach that affected around 209 million users is important. That breach exposed:
- Email addresses
- Display names and usernames (handles)
- Followers count and account creation dates
At the time, X downplayed the leak, stating that it consisted of publicly available data. Despite the massive exposure of email addresses, they insisted that no sensitive or private information was involved. However, security experts warned that the combination of emails and public data could enable phishing and identity theft on a large scale.
What’s Inside the Alleged 2025 Leak?
The 2025 leak, however, is a completely different beast. Unlike the 2023 leak, it doesn’t contain email addresses, but it does hold a goldmine of profile metadata, including:
- Account creation dates.
- User IDs and screen names.
- Profile descriptions and URLs.
- Location and time zone settings.
- Display names (current and from 2021).
- Followers count from both 2021 and 2025.
- Tweet count and timestamps of the last tweet.
- Friends count, listed count, and favorites count.
- Source of the last tweet (such as TweetDeck or X Web App).
- Status settings (like whether the profile is verified or protected).
The data gives a detailed snapshot of users’ profiles and activity over time, including bios, follower counts from different years, tweet history, and even the app used for the last tweet. But the one thing it doesn’t include is the most sensitive bit: email addresses.
The Data Mashup
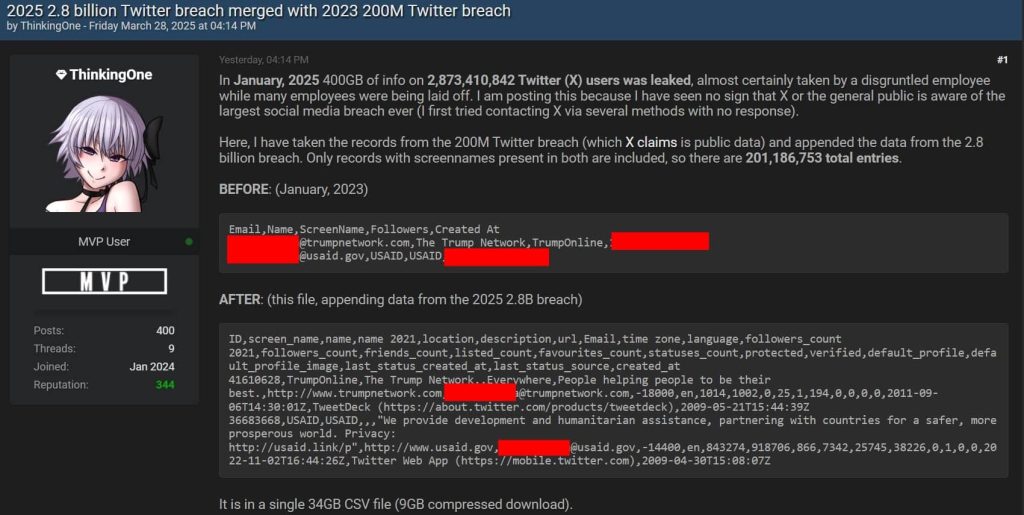
ThinkingOne, a well-known figure on Breach Forums for their skill in analyzing data leaks, decided to combine the 2025 leak with the 2023 one, producing a single 34GB CSV file (9GB compressed) containing 201 million merged entries. To be clear, the merged data only includes users that appeared in both incidents, creating a confusion of public and semi-public data.
This messy combination led many to believe that the 2025 leak also contained email addresses, but that’s not the case. The emails shown in the merged file are from the 2023 breach. The presence of emails in the merged dataset has given the wrong impression that the contents of the 2025 leak also include email addresses.
Why 2.8 Billion Doesn’t Add Up
As of Jan 2025, X (formerly Twitter) had around 335.7 million users, so how is it possible that data from 2.8 billion users has been leaked? One possible explanation is that the dataset includes aggregated or historical data, such as bot accounts that were created and later banned, inactive or deleted accounts that still lingered in historical records, or old data that was merged with newer data, increasing the total number of records.
Additionally, some entries might not even represent real users but could include non-user entities like API accounts, developer bots, deleted or banned profiles that remained logged somewhere, or organization and brand accounts that aren’t tied to individual users.
Another possibility is that the leaked data wasn’t exclusively obtained from Twitter itself but rather scraped from multiple public sources and merged together, including archived data from older leaks or information from third-party services linked to Twitter accounts.
Who Is ThinkingOne, and How Did They Get the Data?
One of the biggest mysteries is how ThinkingOne managed to obtain the 2025 leaked data in the first place. Unlike typical hackers, they are not known for breaching systems themselves but are highly regarded for analyzing and interpreting leaked datasets. Whether they received the data from another source or conducted some sophisticated data aggregation is still unclear.
Their theory that a disgruntled employee leaked the data during the layoffs remains unconfirmed, and there’s no concrete evidence to support it; it is only a plausible hypothesis given the timing and internal mess at X.
Why the Silence from X?
If the claims are true, this is not just a massive data leak in size but also a blow to user privacy. Additionally, whether this was an inside job or not, users are left with more questions than answers: How much of their data has been “taken”? Who’s behind the leak? And why hasn’t X said anything about it, even after ThinkingOne tried reaching out multiple times?











The latest I’ve seen is that X itself estimates around 650 million users. I’m not an X fan by any means but how could a leak of 2.8B users be true?
You are spon on. However, this data could easily be a mix of all kinds of stuff – bots, deleted profiles, suspended accounts, test accounts from X, business accounts, and even data pulled from third-party social media tools or APIs, especially where users signed up with Google, Facebook, or Apple accounts. One thing I know for a fact is that “ThinkingOne”, the person who posted the data, has a solid rep for analyzing leaks and calling out fakes, so I doubt they’d put something out there that doesn’t add up. Still, it’s a messy situation, and it’s weird that X hasn’t responded to any of this, even though ThinkingOne says they tried reaching out. Let’s see if they finally speak up.
The 650M v 2.8B discrepancy is that the 650M number is “Monthly Active Users” (MAU), which are accounts showing some type of activity in the previous month. I’ve gone through a random sample of the screennames (there are almost no duplicates) and checked to see if they were valid X accounts (going to x.com/screenname), and most were (I’m guessing the ones that did not show up as valid accounts were ones the person deleted after the breach). The dataset appears to include suspended/deleted accounts, and probably a lot of bots (but very hard to know which are bots). Roughly 55% posted at least one status update.