Cybersecurity researchers at Kaspersky’s Securelist have found a cyber espionage group known as Angry Likho APT (also referred to as Sticky Werewolf by some security vendors) has reemerged with a new wave of cyberattacks, primarily targeting organizations in Russia and Belarus.
This group, which has been active since 2023, shares similarities with the previously analyzed Awaken Likho group, and is linked to cyber attacks against government agencies and large corporate contractors in Russia and parts of Belarus.
Who Are They Targeting?
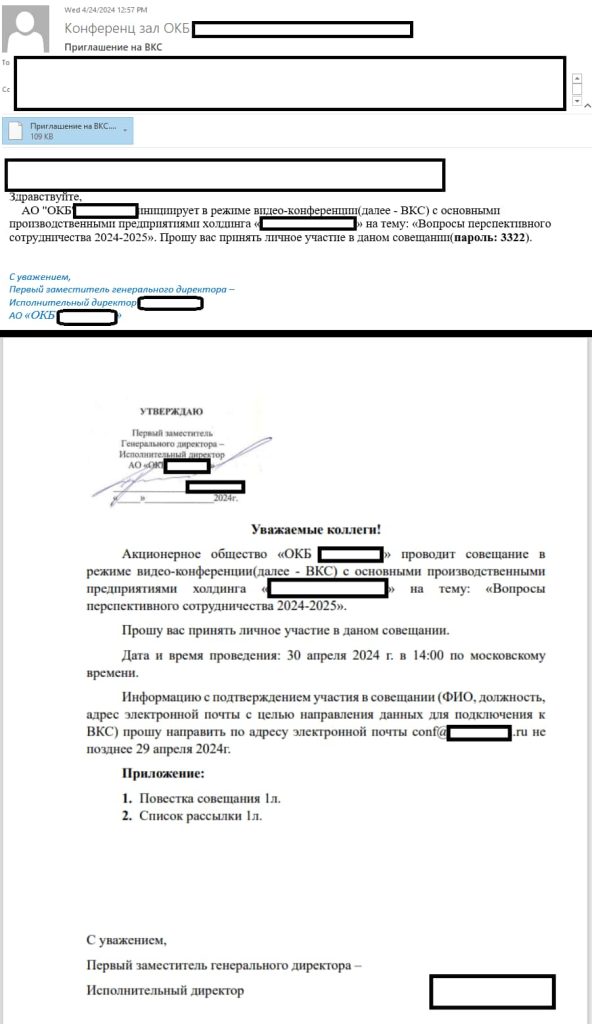
Angry Likho APT has a history of sending highly targeted spear-phishing emails, focusing on employees of large organizations, including government agencies and their contractors. These messages come with malicious RAR files that include harmful shortcut files along with an apparently harmless document.
Once opened, the archive triggers a complex infection chain, ultimately deploying a stealer malware known as Lumma Stealer.
The group’s phishing emails and bait files are written in fluent Russian, suggesting the attackers are likely native Russian speakers. While the majority of victims are in Russia and Belarus, some incidental targets have been identified in other countries, possibly researchers or users of Tor and VPN networks.
According to Securelist’s technical details put together in its blog post, in June 2024, researchers discovered a new implant associated with Angry Likho APT, distributed under the name FrameworkSurvivor.exe. This implant, created using the legitimate Nullsoft Scriptable Install System, functions as a self-extracting archive (SFX).
Upon execution, it extracts files into a folder named $INTERNET_CACHE and launches a heavily obfuscated command file, Helping.cmd. This file, in turn, executes a malicious AutoIt script, which injects the Lumma stealer into the system.
What Does Lumma Stealer Do?
The Lumma stealer is designed to harvest sensitive data from infected devices. It collects system information, installed software details, and personal data such as cookies, usernames, passwords, banking card numbers, and connection logs. It also targets data from popular browsers like Chrome, Firefox, and Opera, as well as cryptocurrency wallets and extensions like MetaMask and Authenticator.
Recent Activity
In January 2025, Russian cybersecurity firm F6 ( (previously F.A.C.C.T) reported new attacks from Angry Likho APT. These attacks involved image files (e.g., test.jpg and test2.jpg) containing Base64-encoded malicious payloads, a tactic previously observed in 2024.
Researchers also identified several new command servers used by Angry Likho, including domains like averageorganicfallfawshop and distincttangyflippanshop. By analyzing these servers, they uncovered over 60 malicious implants, some of which shared the same payload. This suggests the group is actively expanding its infrastructure to evade analysis and detection.
Nevertheless, the research shows that Angry Likho continues to operate consistently, though in a predictable manner. While they make small changes each time, their approach stays the same: targeted phishing emails, a self-extracting archive, and a final payload designed to steal sensitive data.