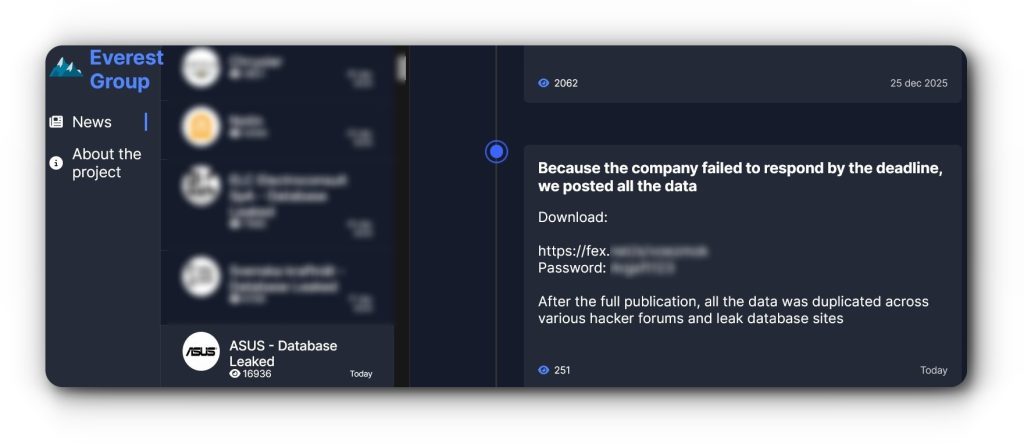
On December 2, 2025, Hackread.com exclusively reported that the Everest ransomware group claimed to have stolen 1TB of sensitive ASUS data, including information related to the company’s AI models, memory dumps, and calibration files. ASUS later confirmed the report and acknowledged the breach, attributing it to a third-party vendor.
Everest has now leaked the entire dataset online. The release followed the group’s claim that ASUS failed to meet the deadline to initiate contact. Notably, the ransomware gang had given the tech giant 24 hours to respond, following its usual approach of demanding a ransom.
As noted by Hackread.com, the leaked data is now circulating on various Russian-language cybercrime forums, including Exploit and DamageLib (formerly and now seized XSS.IS). According to the hackers, the 1TB dump contains nine files, some of which appear to be from ArcSoft and Qualcomm. However, Hackread.com did not download or analyze the leaked material.
This latest leak is part of a series of breaches recently carried out by the Everest ransomware group. Over Christmas, the Russia-linked gang claimed to have breached Chrysler, the American automaker, stating it had stolen 1TB of data. The group described it as a complete database tied to Chrysler operations, along with more than 105GB of Salesforce-related information.
In November 2025, the ransomware group claimed responsibility for breaching Under Armour, stealing 343GB of data, which it later leaked online. The company is now facing multiple lawsuits as a result of the breach. Additional breaches, leaks, and claims by the Everest ransomware group can be found here.
Everest’s latest leak adds to a growing list of big-name targets, and the group shows no signs of slowing down. For ASUS and other companies hit in recent months, the focus should be figuring out exactly what was exposed and increasing their security before it happens again.